Search the Community
Showing results for tags 'SSL'.
-
I just made the switch to using SSL for Emby and wanted to help anyone who is looking for an SSL certificate. I didn't want to spend a lot, as you know some are like $100 a year. I found this place https://www.ssls.com/ssl-certificates/comodo-positivessl They are cheap, $5 a year, but it is a slight pain in the butt for using with Emby. If you go with them you will need to convert the certificate to a compatible version. Plus if you are only running a sub-domain or domain without a web host or e-mail provider like me it is a bigger pain in the butt. For the price you cannot go wrong but be ready to spend an hour or two setting it up with their technical support team.
-
I have spent alot of time trying to make Emby secure with https and I have now hit a brick wall. My knowledge on this topic is zero, so im hoping with some guidance I can get this working. OS: Windows Port Forward: 443 Domain: YES SSL: Lets Encrypt via Win-Acme (No passphrase) Reverse Proxy: NGINX Most of the infomation is taken from https://emby.media/community/index.php?/topic/44757-setting-up-ssl-for-emby-wip/#comment-419091 Where I have hit a brick wall is when i try and start NGINX. It fails to start and nothing shows in the logs. Below is my nginx.conf, Thanks in advance. worker_processes 2; events { worker_connections 8192; } http { include mime.types; default_type application/octet-stream; server_tokens off; gzip on; gzip_disable "msie6"; gzip_comp_level 6; gzip_min_length 1100; gzip_buffers 16 8k; gzip_proxied any; gzip_types text/plain text/css text/js text/xml text/javascript application/javascript application/x-javascript application/json application/xml application/rss+xml image/svg+xml; tcp_nodelay on; sendfile off; server_names_hash_bucket_size 128; map_hash_bucket_size 64; ## Start: Timeouts ## client_body_timeout 10; client_header_timeout 10; keepalive_timeout 30; send_timeout 10; keepalive_requests 10; ## End: Timeouts ## ## Default Listening ## server { listen 80 default_server; listen [::]:80 default_server; server_name _; return 301 https://$host$request_uri; } ##EMBY Server## server { listen [::]:80; listen 80; listen [::]:443 ssl; listen 443 ssl; server_name emby.mydomain.com; ssl_session_timeout 30m; ssl_protocols TLSv1.2 TLSv1.1 TLSv1; ssl_certificate C:\\nginx-1.26.2\conf\SSL\mydomain.com-crt.pem; ssl_certificate_key C:\\nginx-1.26.2\conf\SSL\mydomain.com-key.pem; ssl_session_cache shared:SSL:10m; ssl_prefer_server_ciphers on; ssl_ciphers ECDH+AESGCM:ECDH+AES256:ECDH+AES128:DH+3DES:!ADH:!AECDH:!MD5; proxy_hide_header X-Powered-By; add_header X-Xss-Protection "1; mode=block" always; add_header X-Content-Type-Options "nosniff" always; add_header Strict-Transport-Security "max-age=2592000; includeSubdomains" always; add_header X-Frame-Options "SAMEORIGIN" always; add_header 'Referrer-Policy' 'no-referrer'; add_header Content-Security-Policy "frame-ancestors mydomain.com; emby.mydomain.com; location / { proxy_pass http://192.xxx.xxx.xxx:8096; proxy_hide_header X-Powered-By; proxy_set_header Range $http_range; proxy_set_header If-Range $http_if_range; proxy_set_header X-Real-IP $remote_addr; proxy_set_header Host $host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; #Next three lines allow websockets proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } } }
-
I read through the SSL Made Easy tome. The original post showing instructions for ssl setup was good (although I already knew it) but the rest did nothing for me. I'd like to describe my SSL problem and hopefully get some ideas for what I'm doing wrong. I used certbot to create the privkey.pem and cert.pem files. Then I did I left the password blank. The resulting emby.p12 file looks good. I extracted the key file from it which matched the original. Then I set the network settings to... It saved with no problem. Then I rebooted the server. The address "http://<domain>:8096/" worked fine. I tried the address: "https://<domain>:8920" and got "<domain> refused to connect." I have no proxy or firewall. Others can try these URLS from outside but they will only get the login page. The log from the reboot I mentioned is attached. By an amazing coincidence the log starts at exactly midnight. Any ideas for things to try would be appreciated. embyserver (3).txt
-

[How-To] Emby Server on Windows Server with IIS as Reverse Proxy with Automatic Certificate Renewal
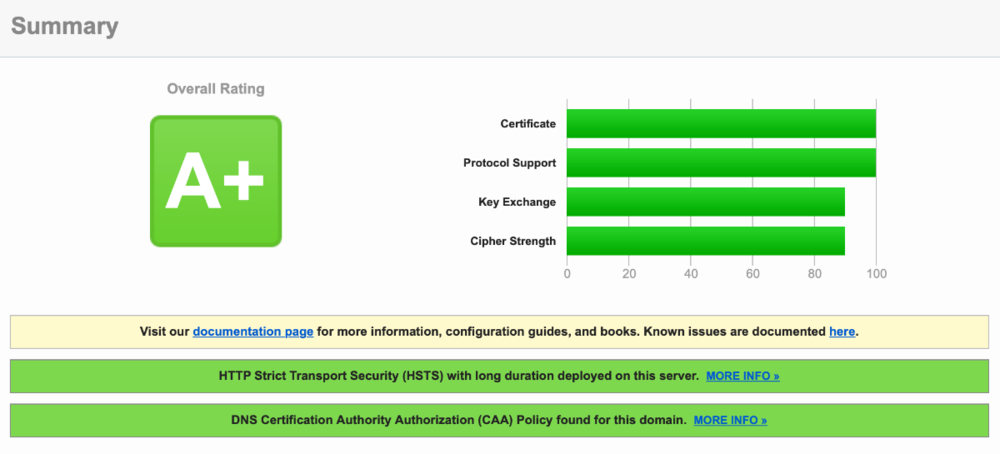
TheITJedi posted a topic in General/Windows
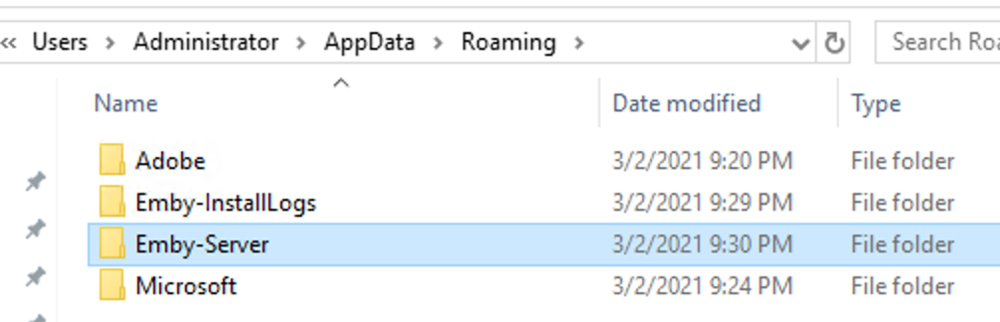
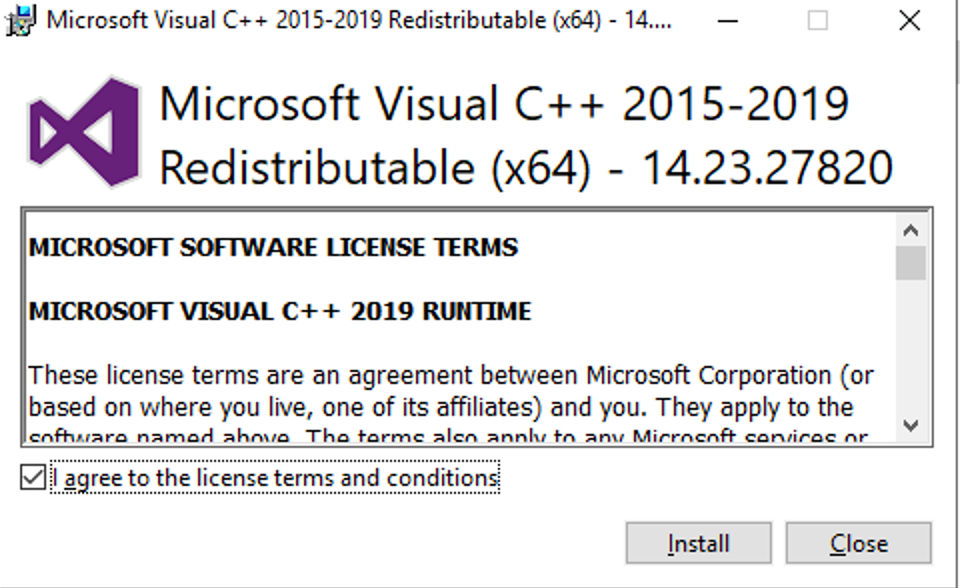
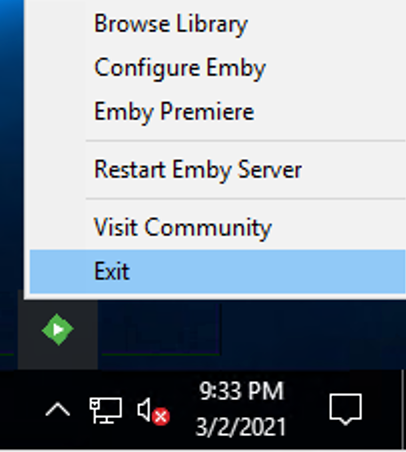
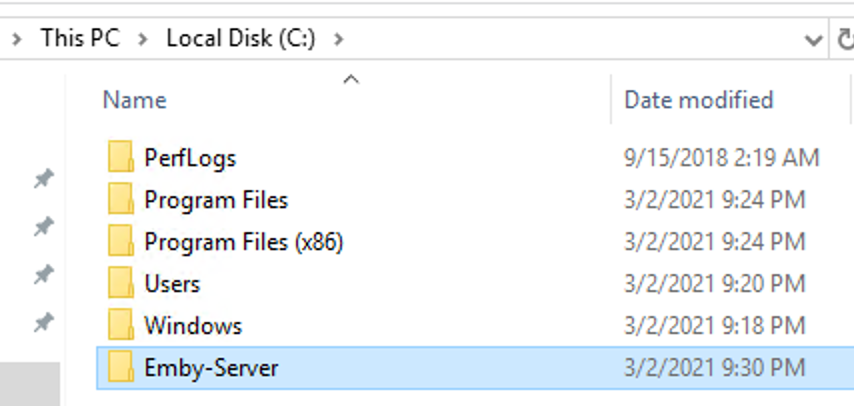
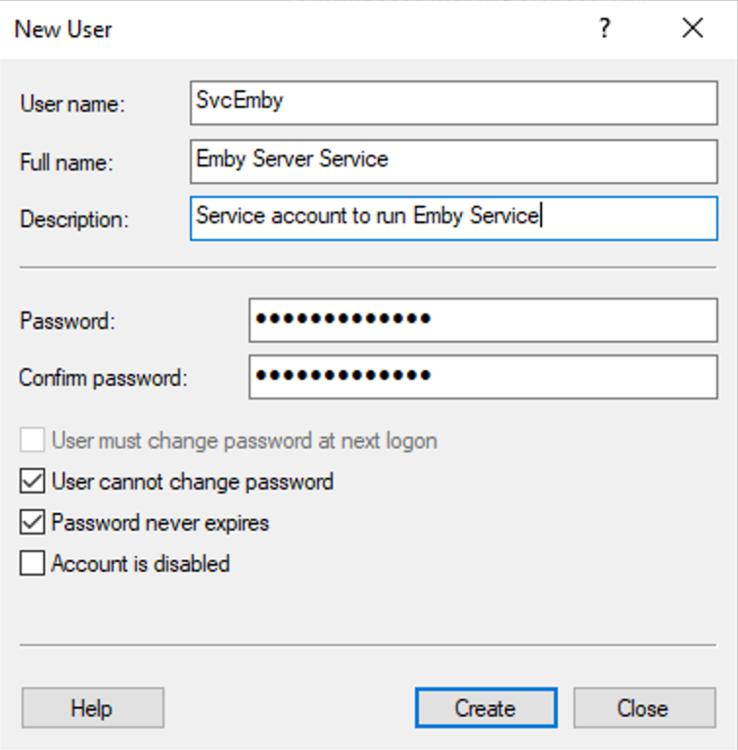
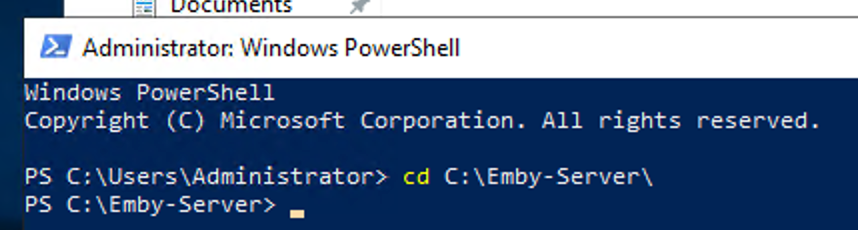
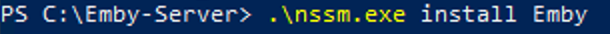
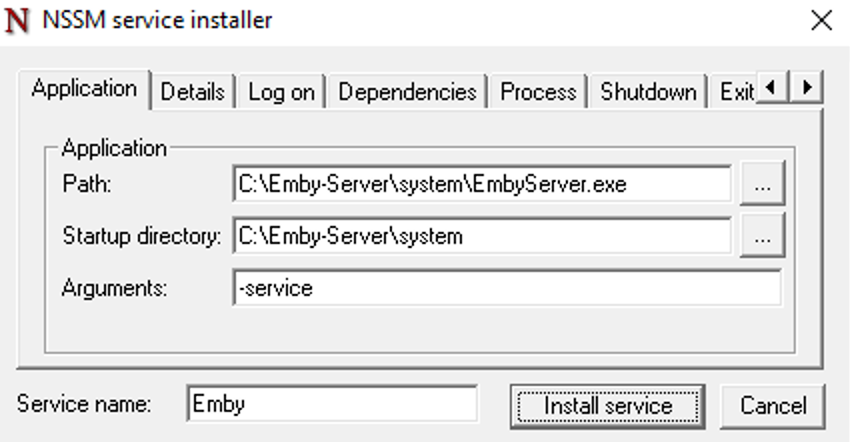
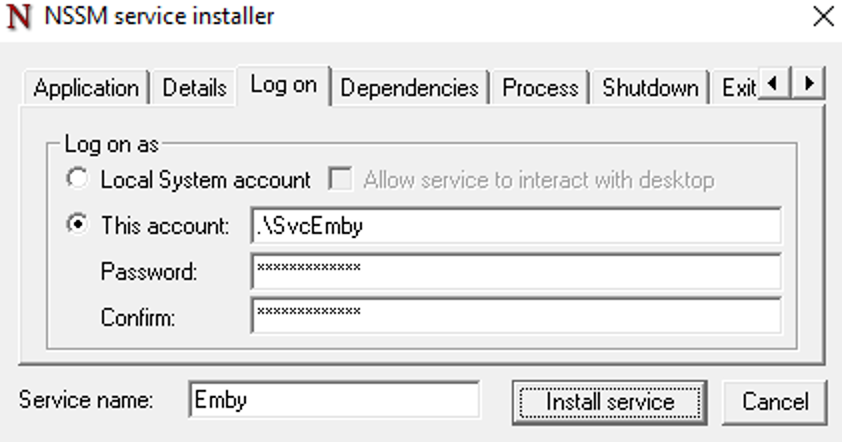
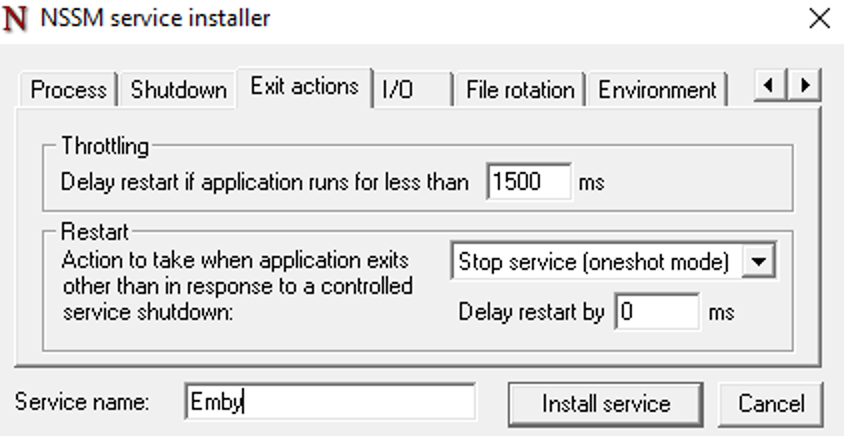
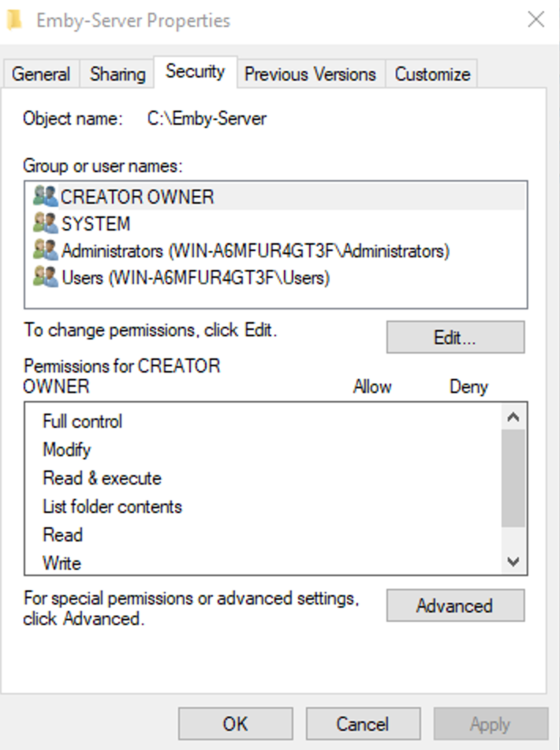
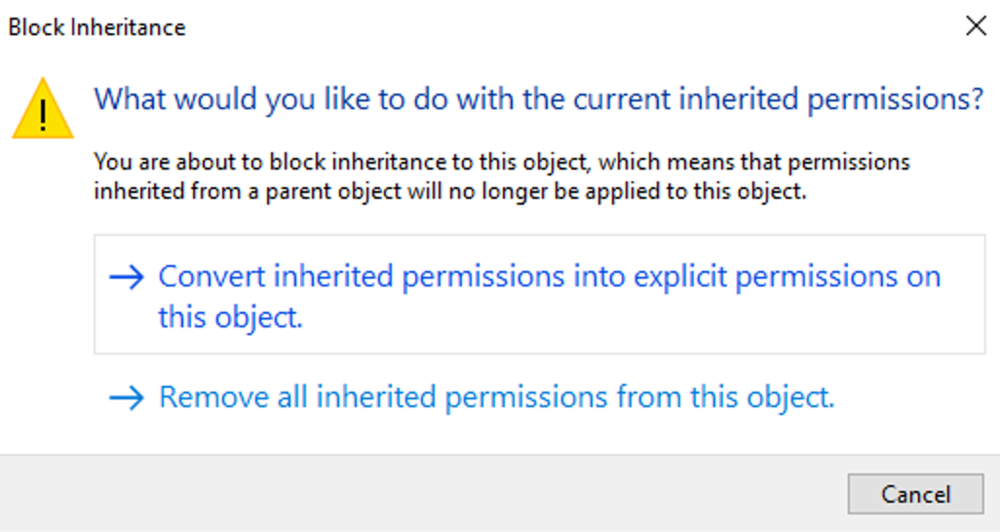
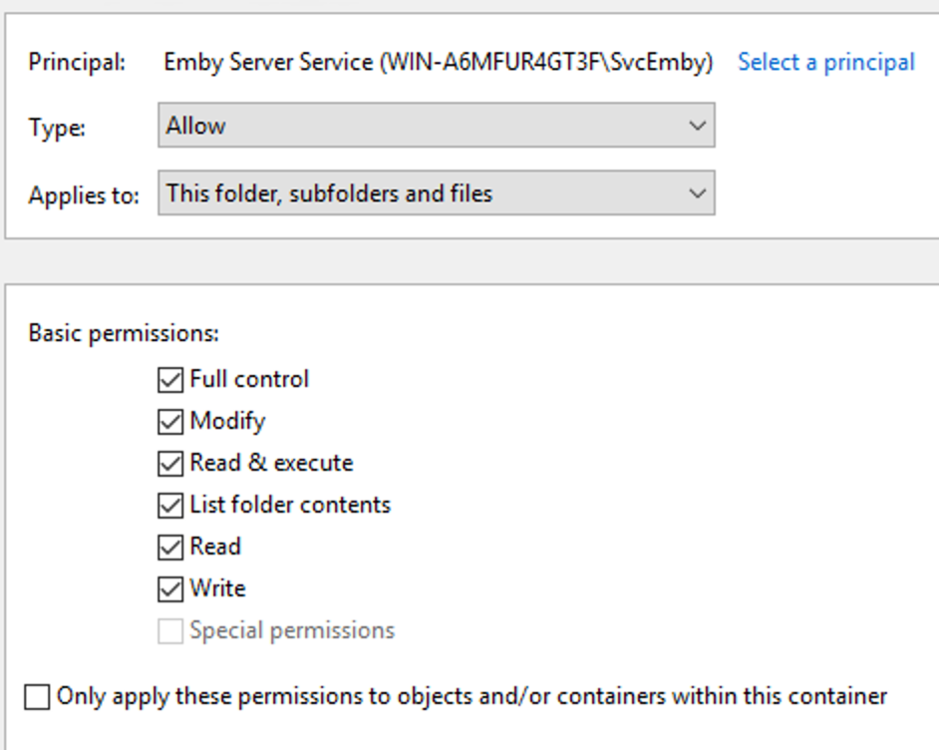
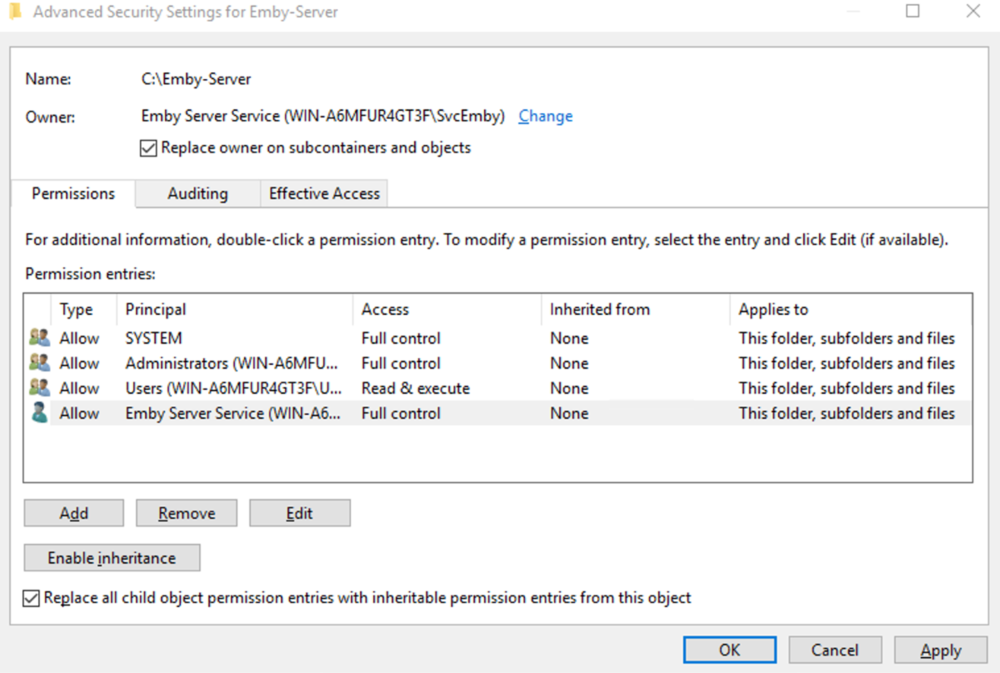
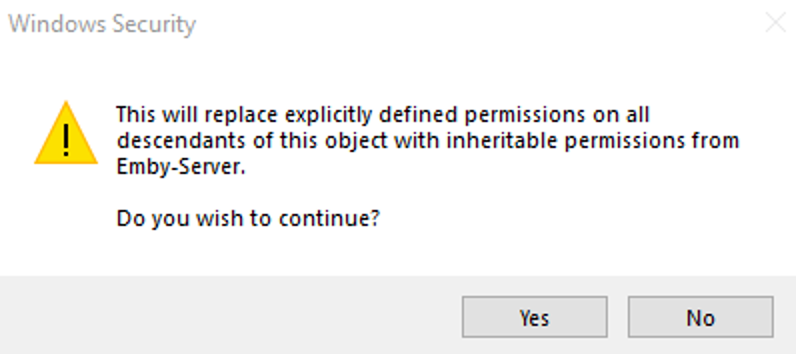
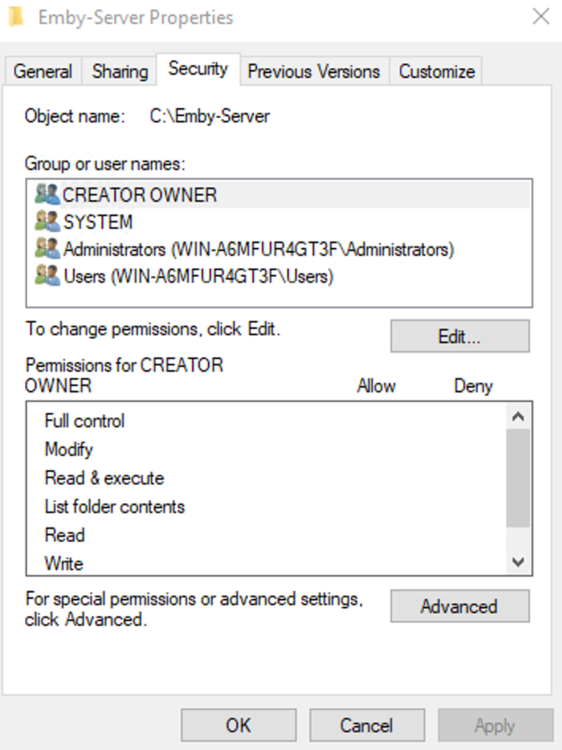
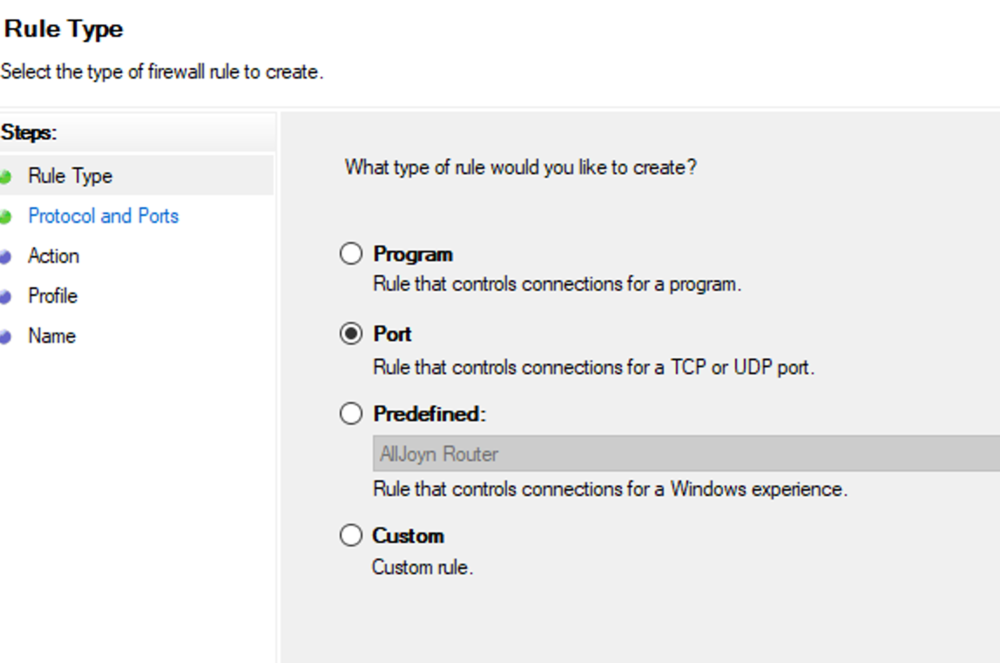
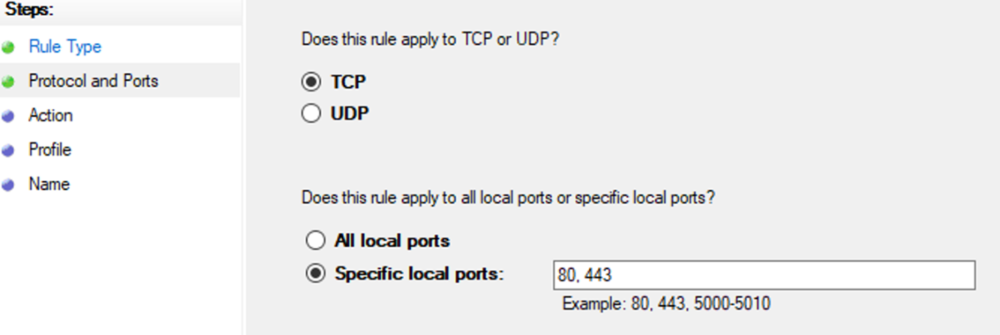
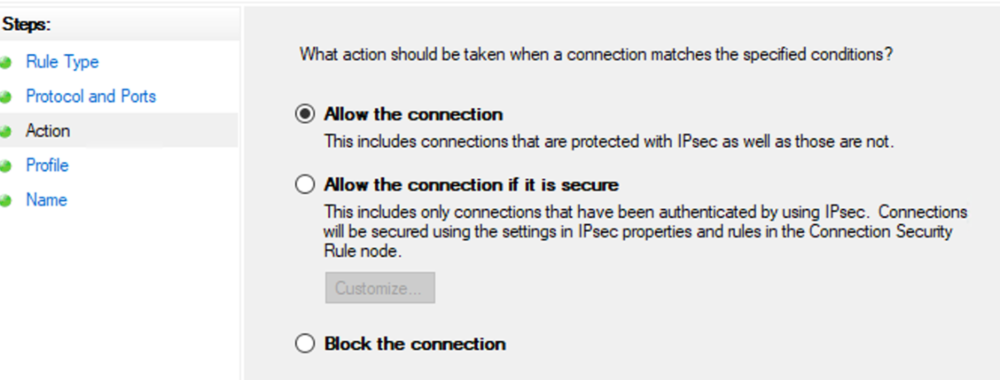
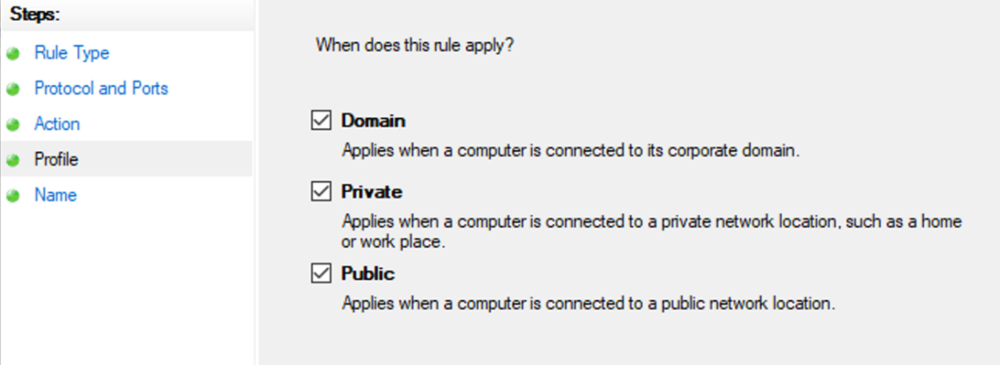
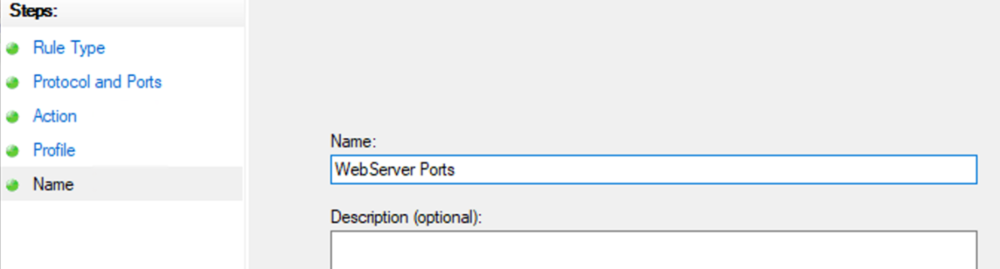
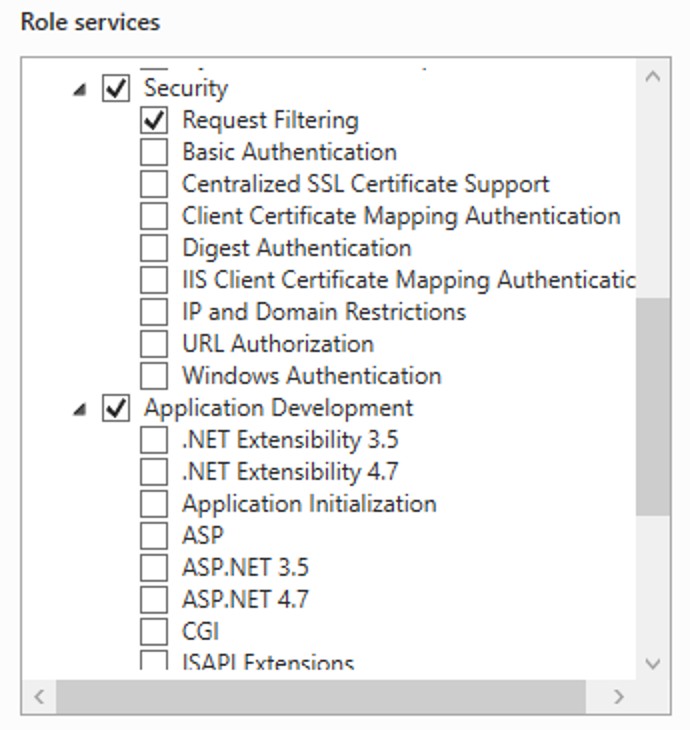
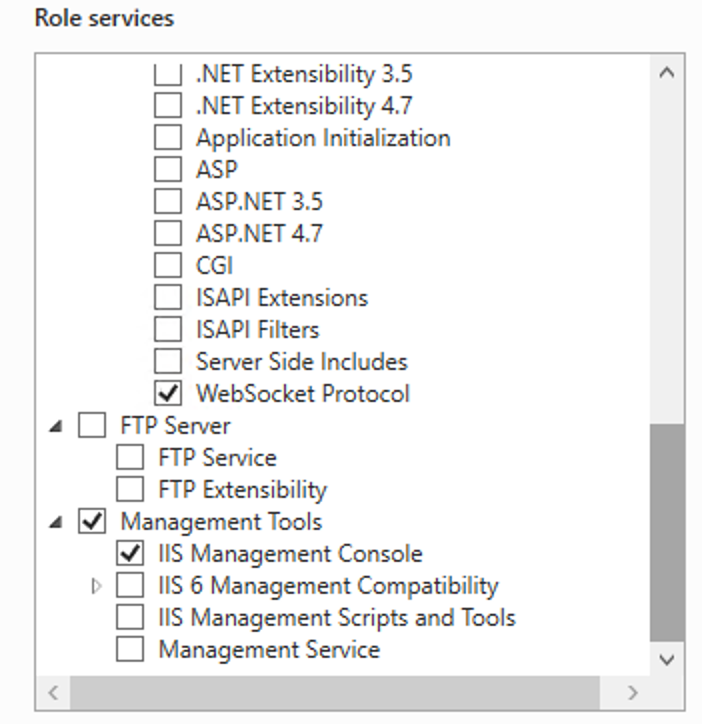
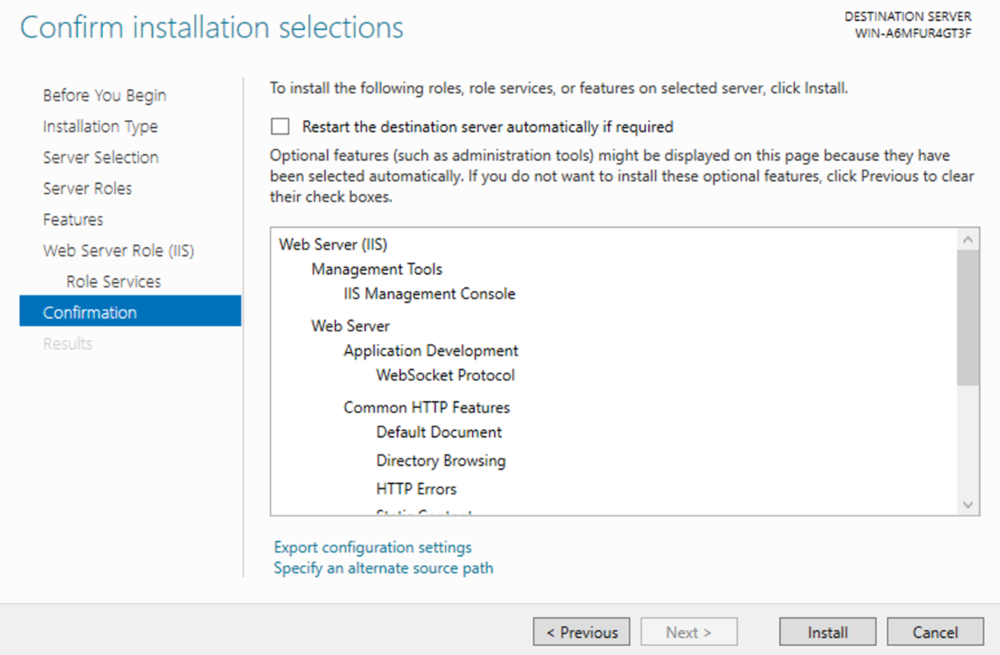
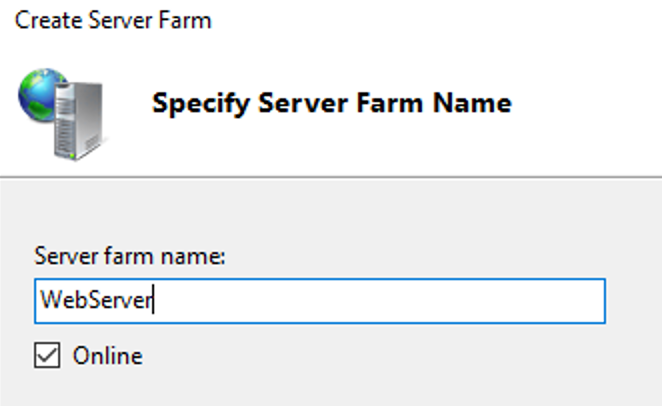
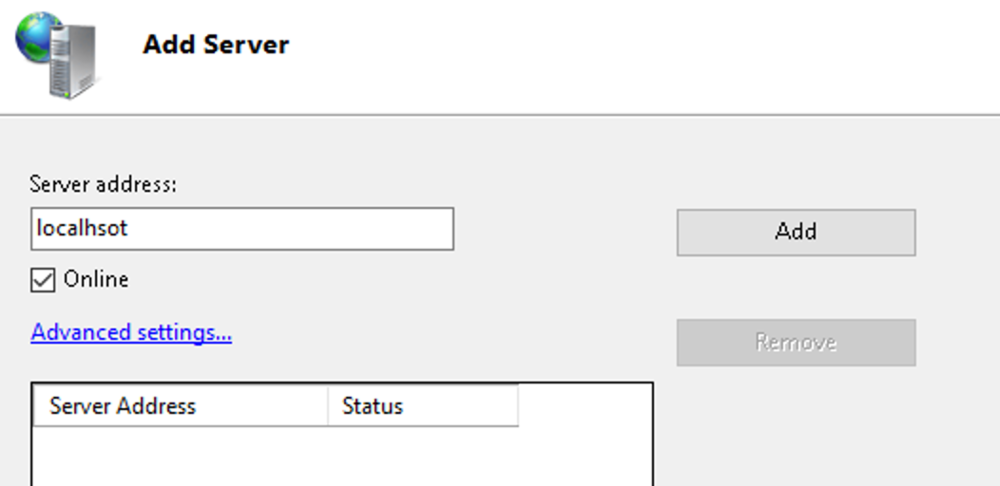
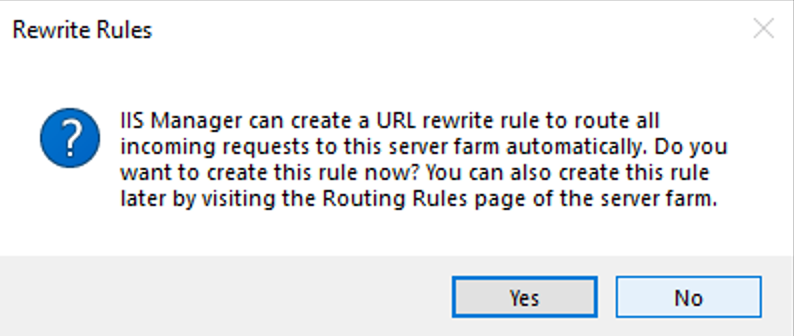
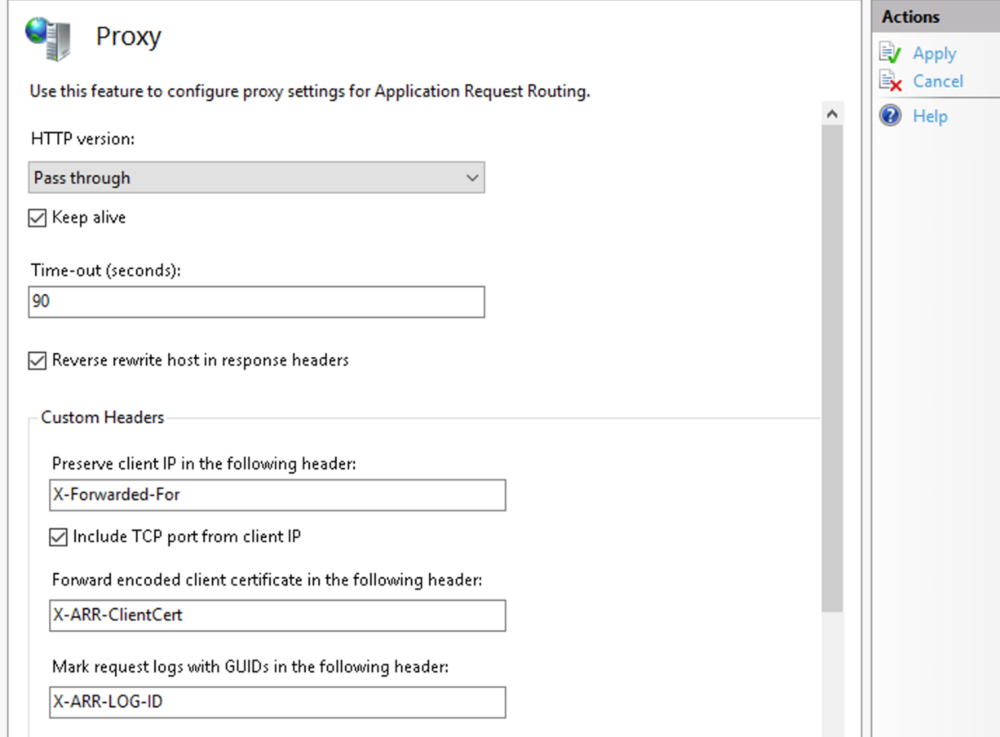
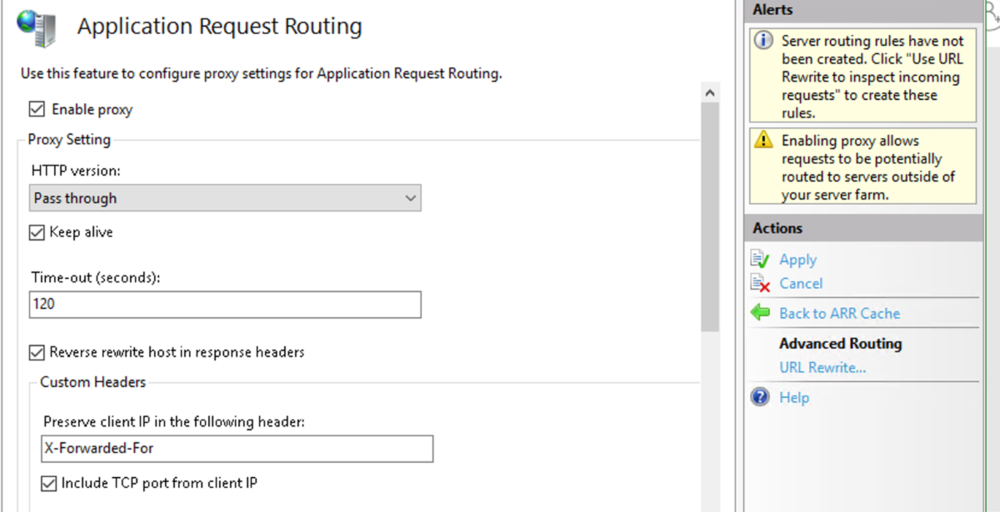
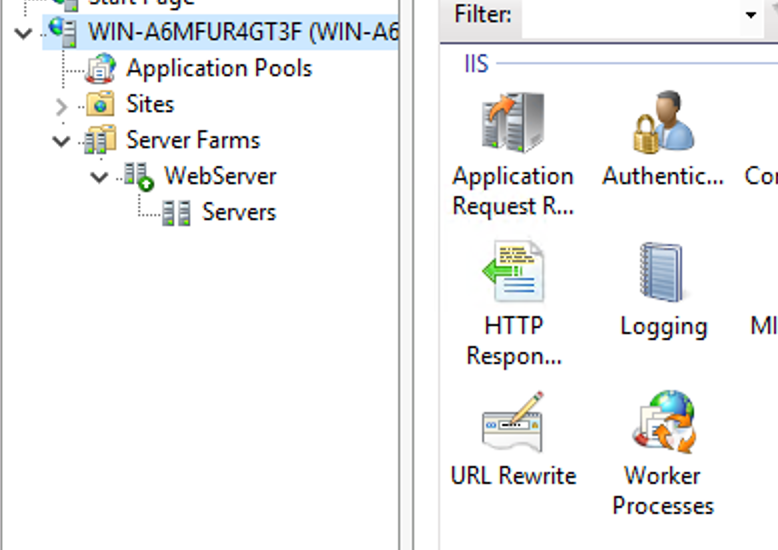
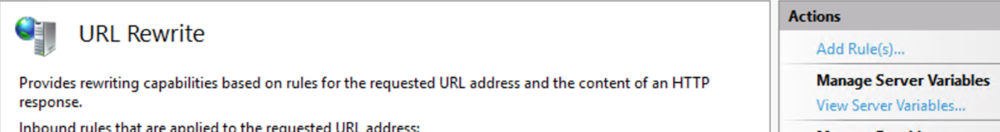
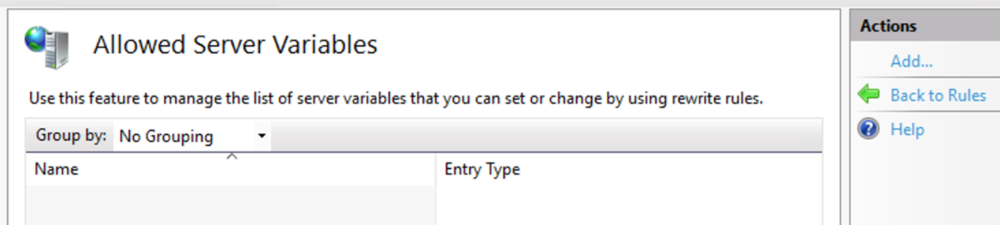
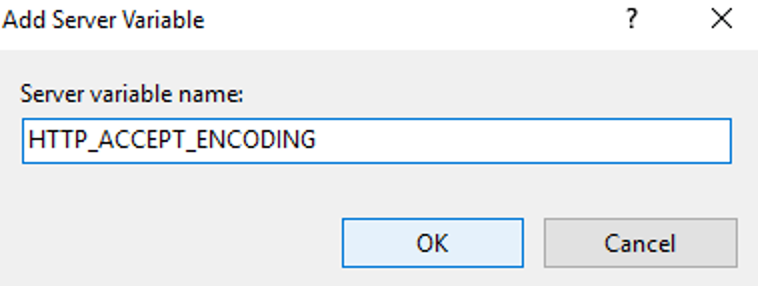
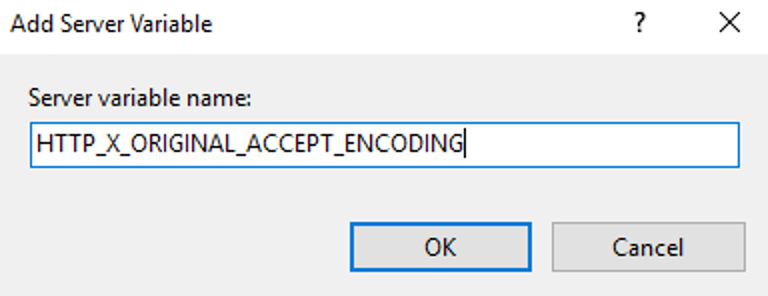
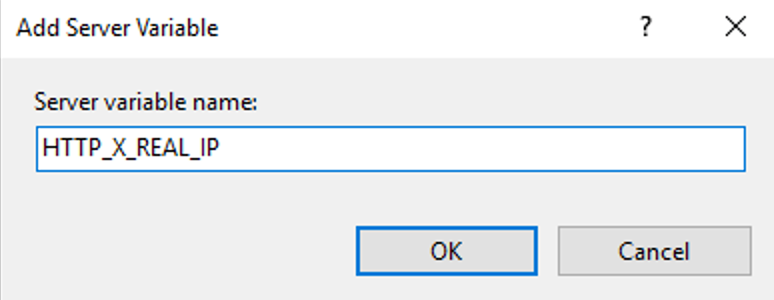
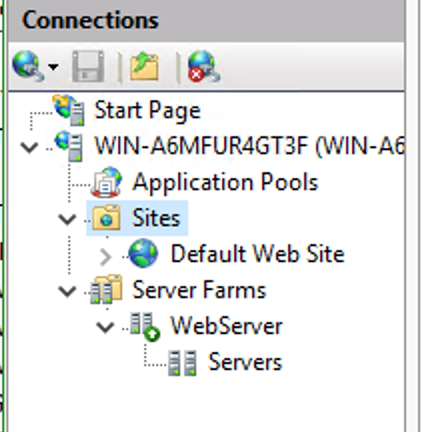
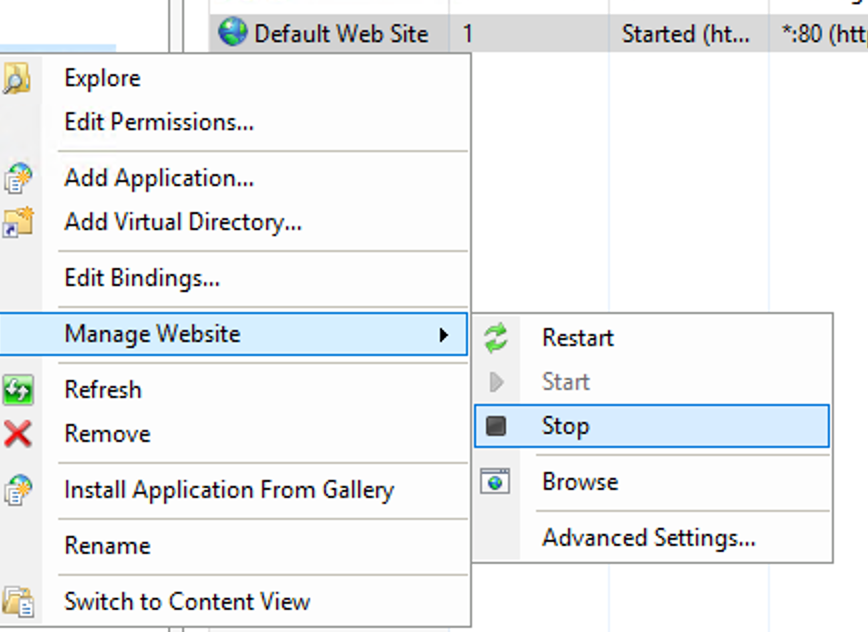
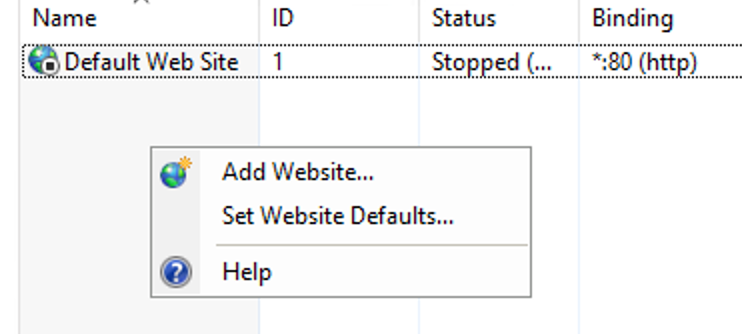
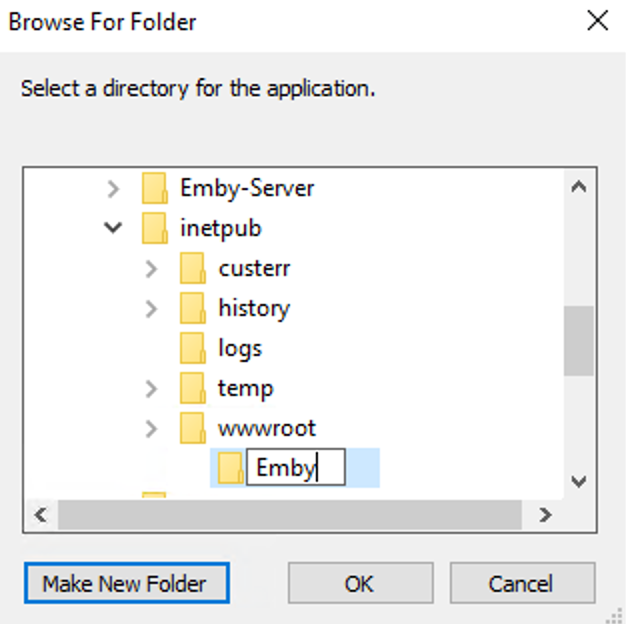
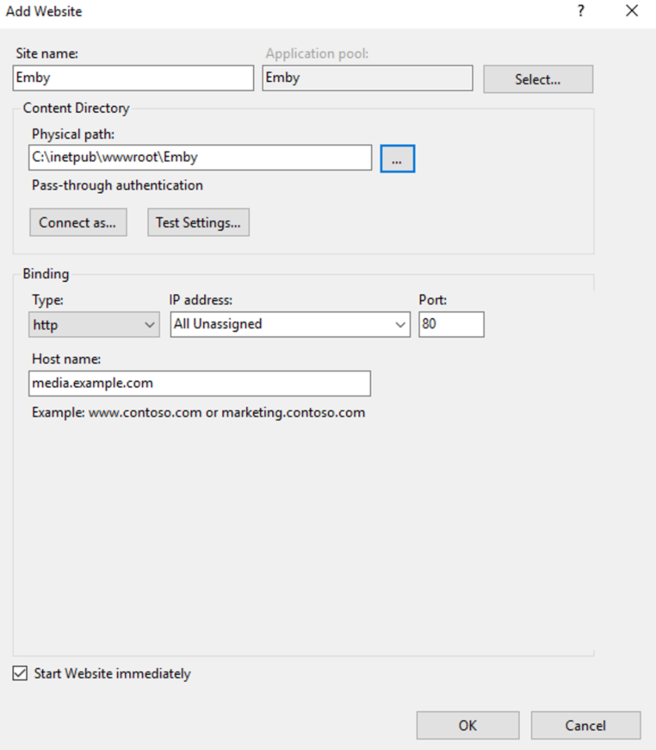
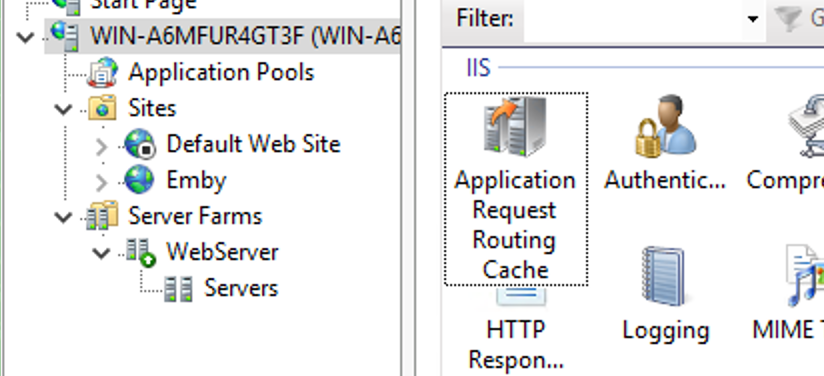
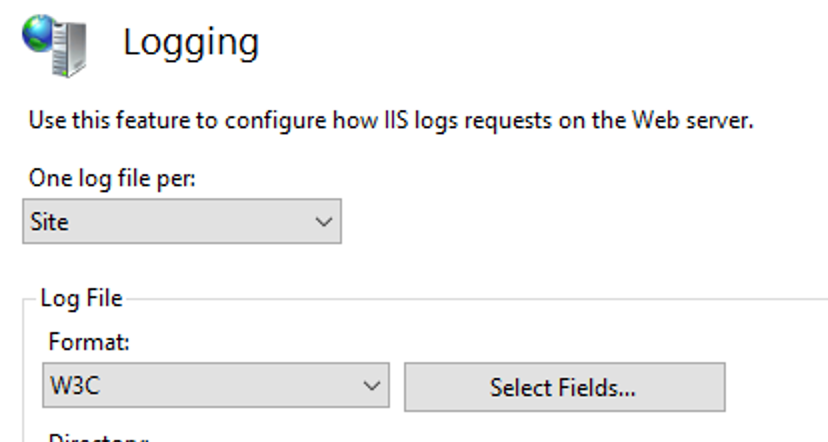
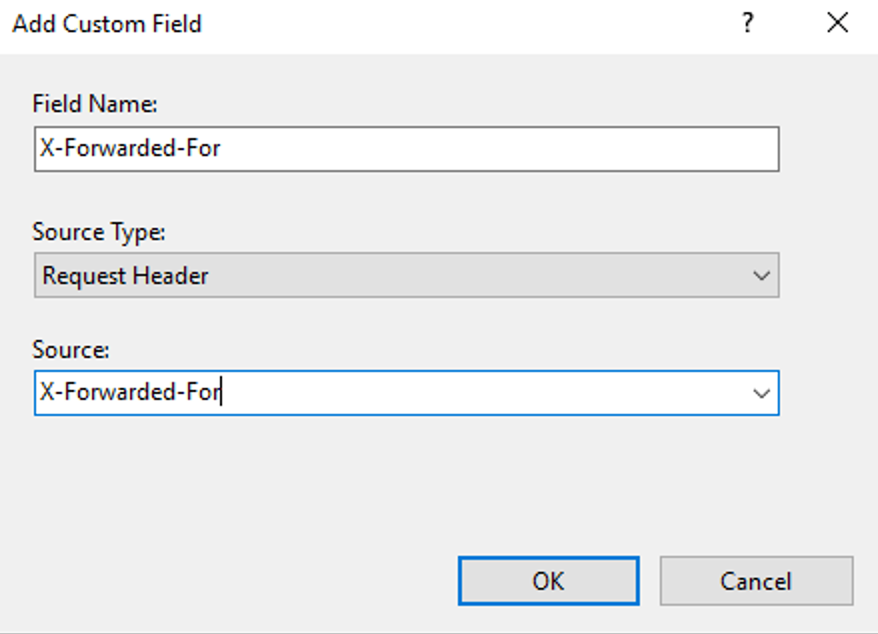
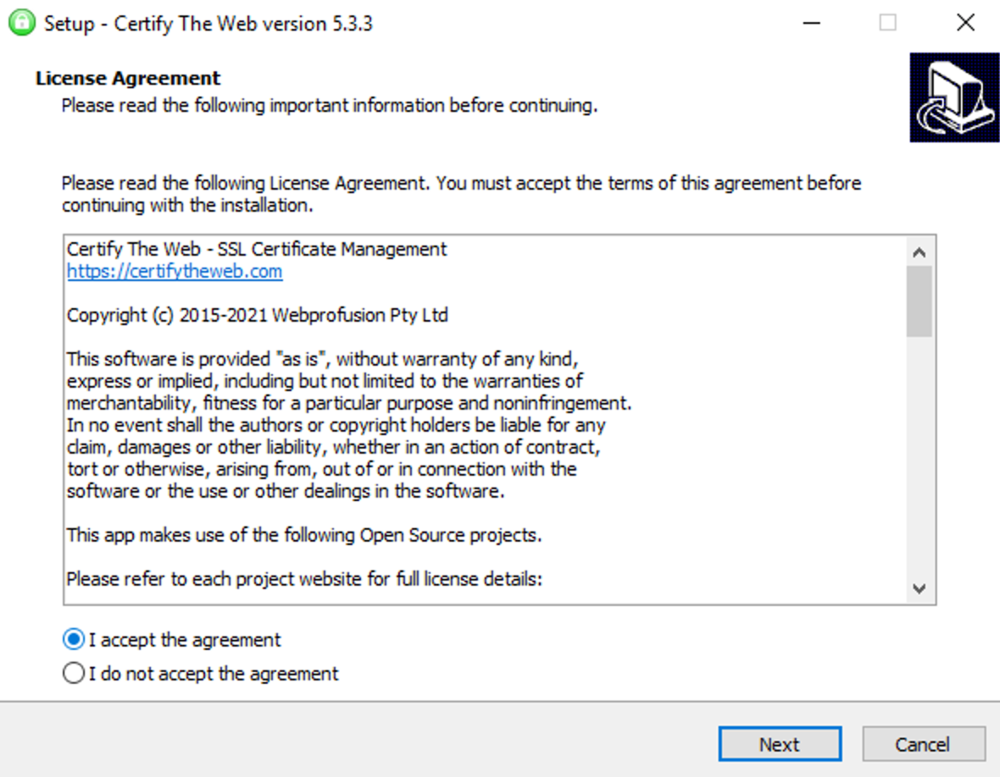
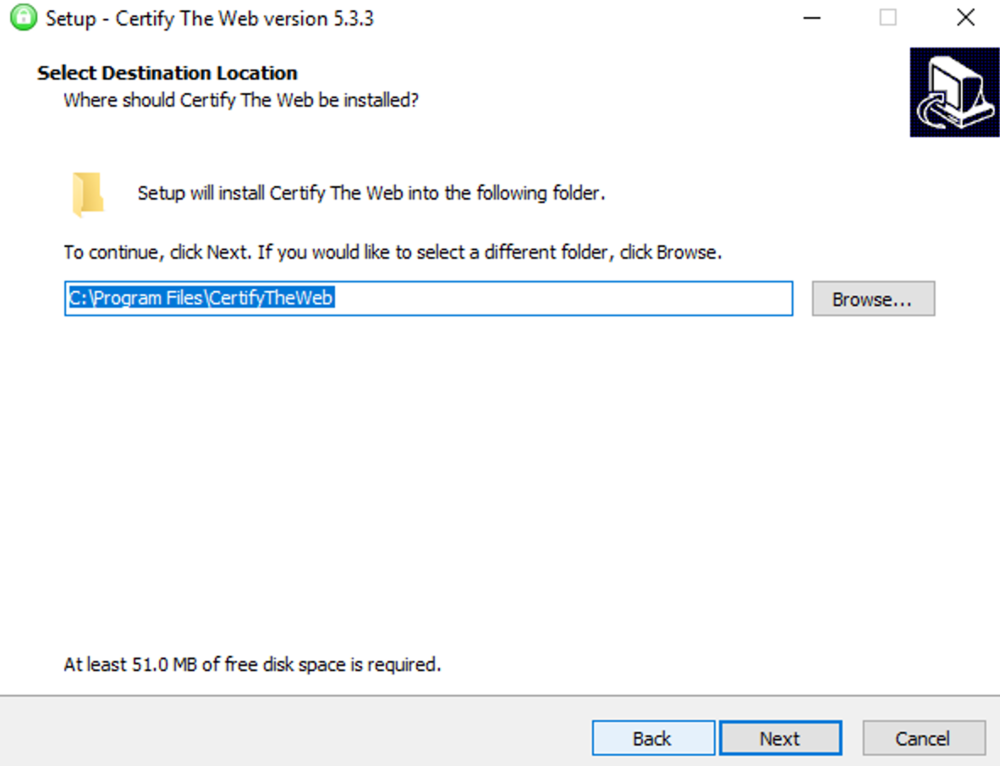
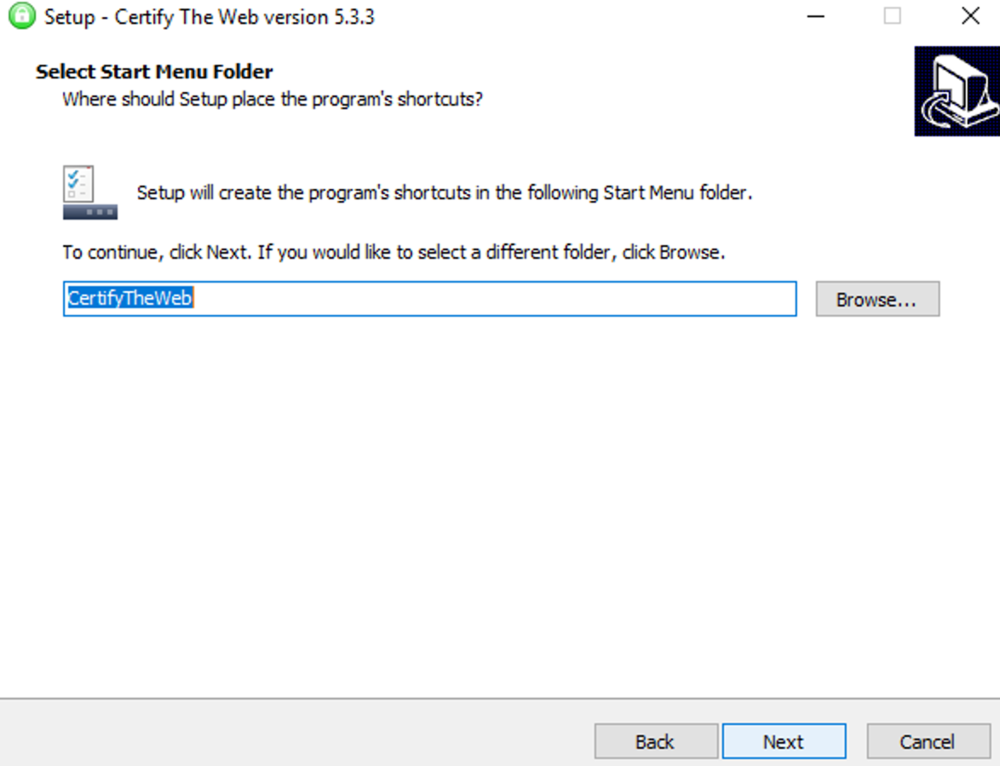
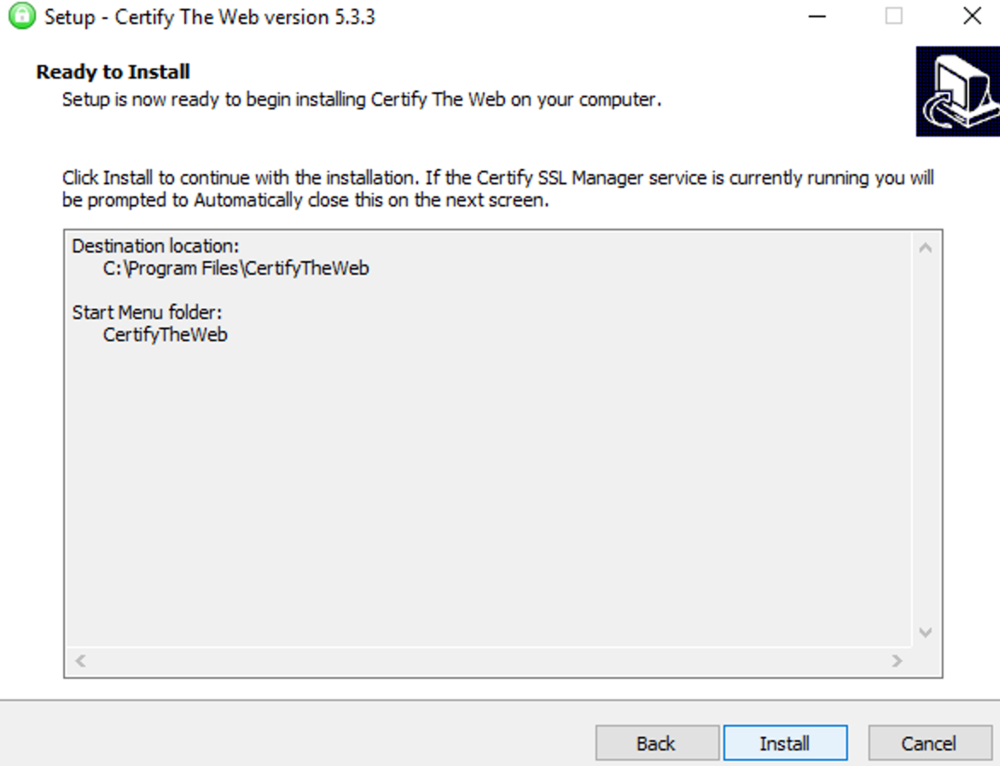
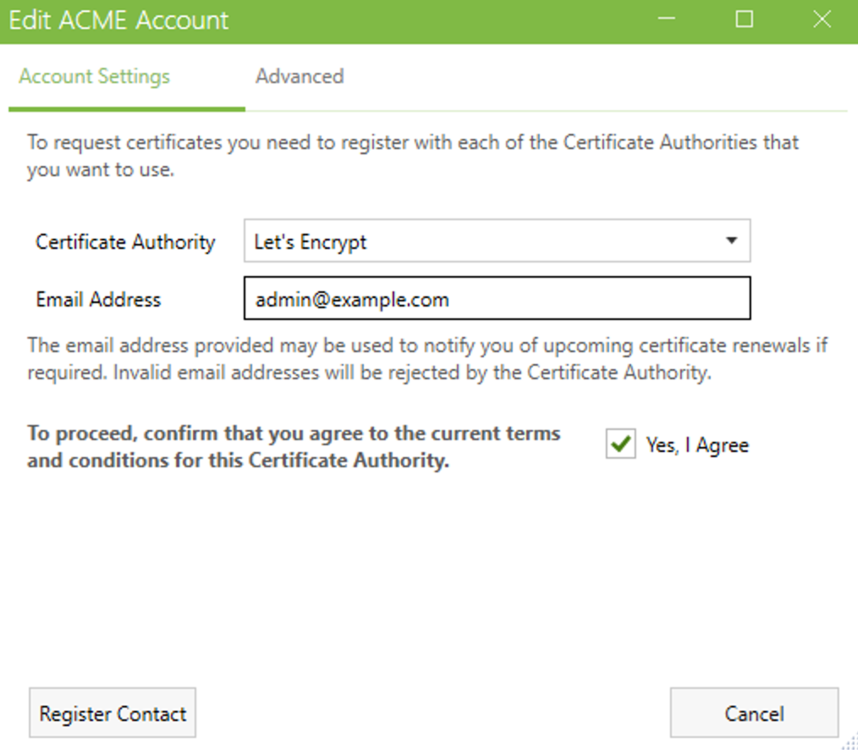
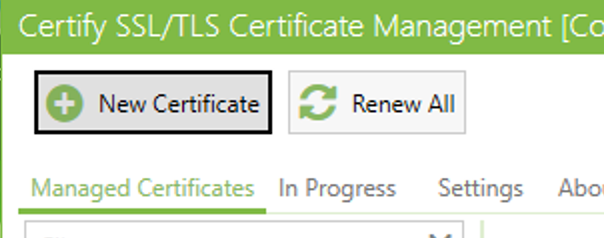
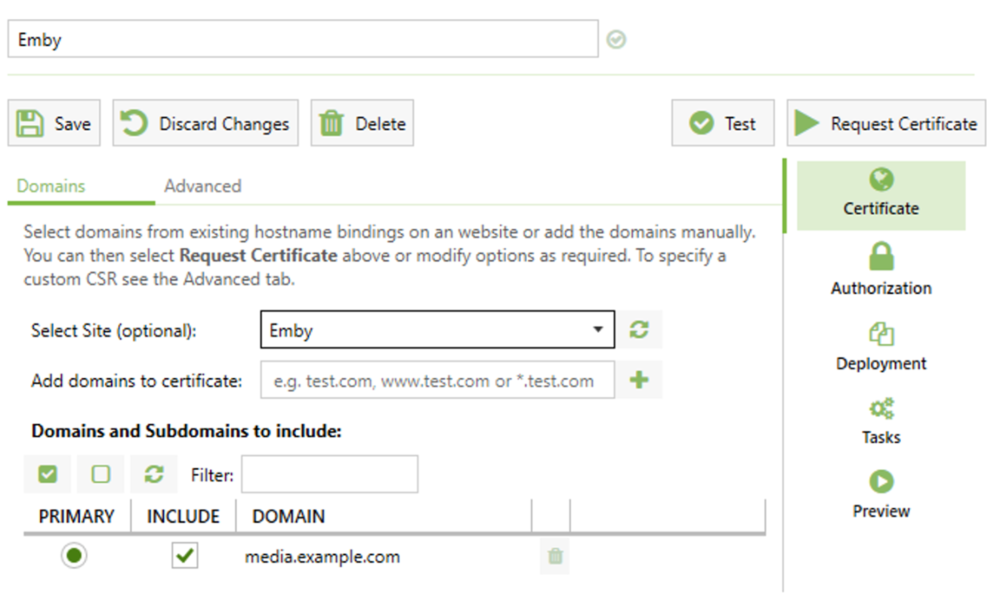
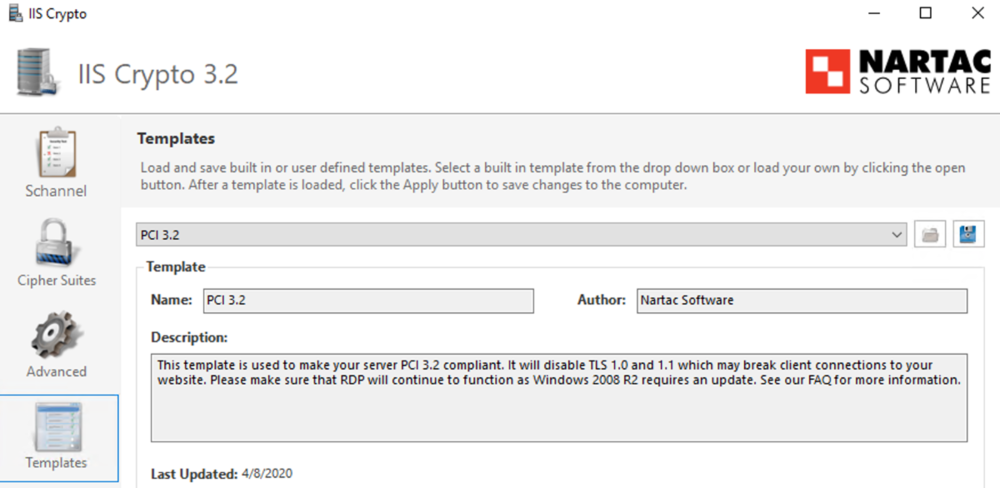
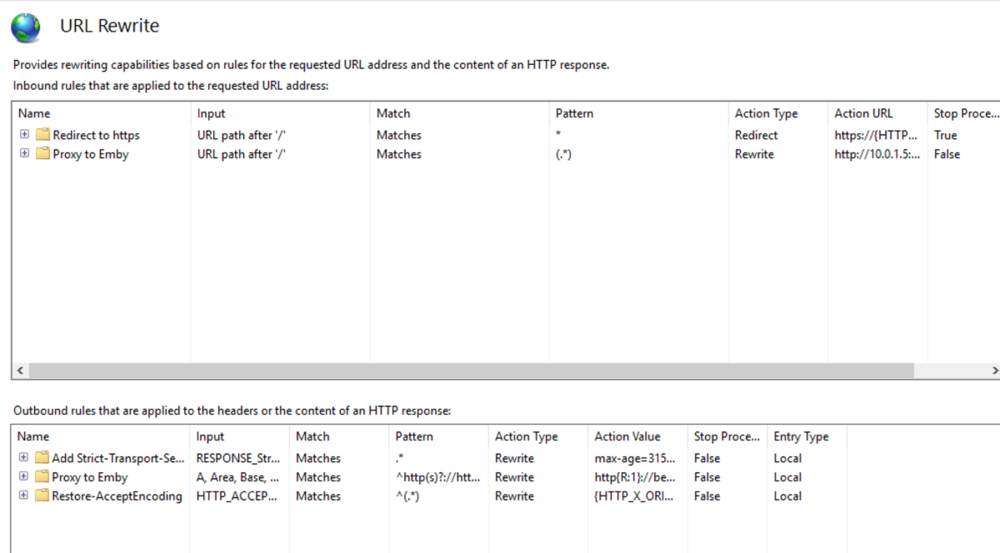
This guide will explain how to setup a Windows Server instance of Emby server with IIS as full transparent reverse proxy with SSL offload and auto-renewing certificates via Lets Encrypt. First, What is IIS? IIS or Internet Information Services is the web server service provided with Windows and Windows server installations. It is industry standard technology and is widely supported and regularly maintained by Microsoft. Second, What is a reverse proxy? A reverse proxy will take requests coming into your server (in this case HTTPS on port 443) and route them to a backend application (in this case Emby Server on port 8096 on the same box or another). Reverse proxies are very useful if you only have 1 public IP and multiple services you would like to run on a single port (443, for example is standard secure web traffic) or multiple servers that need to appear as one. Third, Why do I want a certificate for my site from Lets Encrypt? Well, most sites now days are secure (read they encrypt your traffic to prevent people from seeing your data), browsers these days flag sites that are not using properly signed certificate chains or run on insecure ports. If you use a self signed certificate in Emby, you may have difficulty getting things like the iOS app or Roku app to work properly outside your home. (Not sure about the rest of you, but Emby on the kid’s iPad is a life saver for long car rides). Let’s Encrypt provides free SSL certificates that are signed by certificate authorities that will be recognized on all devices and platforms. I will be using Windows Server 2019 with IIS 10 and AAR 3. All of this should work with Windows Server 2012R2 and Windows Server 2016 as well as Windows 10, however there may be some differences. You can use either stable or beta version of Emby Server, however in this guide we will use the stable version. At the time of writing, this guide will get you a full A+ rating from SSLlabs.com security test. (For comparison purposes, Facebook’s rating is a B.) In this guide we will: Install Emby Server Move Emby Server Installation to a non-user-locked location Setup a service user to run Emby Server as Configure Emby Server to run as a service Configure Windows Firewall Install IIS Install AAR Install IIS Rewrite module Configure AAR Configure IIS as a reverse proxy for Emby Configure SSL cypher suites for the server Install the Certify the Web client. Configure Certify the Web for auto-renewing SSL certificate for your domain Note: To be externally accessible, you will need to configure your route/modem to port forward 80 and 443 to your server. Pre-reqs/Assumptions: A physical server or VM running Windows Server An Internet Connection A DynDNS/No-IP URL (or similar routable dns name pointed at your router’s public IP) You have port forwarded ports 80 and 443 through your router to the machine you will use as a reverse proxy (in this guide we will use the same box for the reverse proxy and Emby server, but these can be run on different hosts). You have installed Notepad++ on the machine you will be setting up. Install Emby Server Download Emby Server Run the Installer Click Run when prompted If prompted by smart screen, click run anyway If prompted to install Visual C++ runtime, click install It will install to default location of %APPDATA%\Emby-Server. Move Emby Server to Non-User Locked Location Ensure that Emby Server is not running (right click icon in system tray if present and click Exit) Navigate to default location of %APPDATA% (%userprofille%\appdata\roaming) Right click the folder and click "cut" Navigate to C:\ (or root of the drive you wish to have Emby run from) Right click in the whitespace and paste. (if prompted to provide administrator permission, approve) Create a Service Account to run Emby as Note: Instructions show how to do this using local users and computers, you can also do this with Active Directory Users and Computers if your server is running that role. Right click on the start button (Windows flag) on the left side of the task bar Click Computer Management Expand Local Users and Groups on the left side Click Users Right click the whitespace and click new user Complete the new user dialog as shown (make sure you save whatever password you use as you will need it later, ProTip: don't re-use passwords) Click create Click close Close the computer management window Setup NSSM NSSM (Non-Sucking Service Manager) is needed to run Emby Server as a service as Emby Server does not include the nessicary components to run as a Windows service by default. Download here: https://nssm.cc/download Double click downloaded zip to open it in windows explorer Navigate to /win64 folder inside zip Copy/extract 64 bit version of the file to C:\Emby-Server Setup Folder Permissions Navigate to C:\ Right click the Emby-Server folder Click Properties Click Security tab Click Advanced Click Disable Inheritance Click Convert to Explicit Select CREATOR OWNER Click Remove Select Users (special) Click Remove Click Add Enter SvcEmby in the dialog Click OK Click Full Control Click OK Click Change next to owner at the top of the box Type SvcEmby in the dialog Click OK Check the Replace owner check box Check the Replace permissions checkbox Verify the dialog window looks similar to this (computer name will be different) Click OK When prompted if you want to replace permissions click Yes Verify security tab looks like this Click OK Setup Emby as a Service using NSSM Right click the start button on the left side of the task bar Click Windows Powershell (Admin) Type: "cd C:\Emby-Server" and press enter Type ".\nssm.exe install Emby" and press enter The install service dialog will launch, fill out as follows: Application Tab Details Tab Logon Tab (note, if you are using active directory it should be: YOURDOMAIN\SvcEmby) Exit Actions Tab Click Install Service Click OK Config ure Windows Firewall Click Start Click Control Panel Click Windows Defender Firewall Click Advanced Settings on the left hand side Click Inbound Rules Click New Rule on the right hand side Click Port Click Next Type 80, 443 in the ports box Click Next Click Next Click Next Name it Web Server Ports Click Finish Install IIS (Internet Information Services) Click Start Click Server Manager Click Add Roles and Features Click next on the Before you Begin page Click Role Based install Click Next Verify you are installing on your local server Click Next Check the box for "Web Server (IIS)" When prompted to install management tools Click Add Features Click Next Under Features, click Next Click Next again to get to role services Check the boxes for all of the following role services Make sure you check the box for web sockets under Application Development, this is needed for various features of Emby to work right. Click Next Click Install Once installation completes, click close Install Web Platform Installer add-on Download from: https://www.microsoft.com/web/downloads/platform.aspx Run the Web Platform Installer add-on installer Click Install Click Finish Install AAR (Advanced Application Routing) Download from: https://www.microsoft.com/en-us/download/details.aspx?id=47333 Run the Request Router installer Click Install Install IIS Re-Write Module Click Start Click Administrative Tools Open Internet Information Services (IIS) Manager Click the name of your server on the left Double Click on the Web Platform Installer In the search box type "url rewrite" Click Add Click Install Click I Agree Click Finish Configure AAR Click Start Click Administrative Tools Open Internet Information Services (IIS) Manager Click the name of your server on the left Right Click Server Farms Click Create Server Farm Name your Server Farm Click Next Enter the IP address of the server or "localhost" Click Add Click Finish Click No in the dialog that pops up Expand your newly created Server Farm Click Proxy Configure settings as shown Click Apply Click your Server Click Application Request Routing Click Server Proxy Settings Configure settings as shown Click Apply Click Your Server Configure IIS Server Variables Click Url Re-Write Click View Server Variables Click Add Type "HTTP_ACCEPT_ENCODING" Click OK Click Add Type "HTTP_X_ORIGINAL_ACCEPT_ENCODING" Click OK Click Add Type "HTTP_X_FORWARDED_FOR" Click OK Click Add Type "HTTP_X_REAL_IP" Click OK Click Your Server Create Emby Site Expand Sites on the left hand side Right Click "Default Web Site" Highlight "Manage Website" Click Stop Right Click the white space in the Sites list Click Add Website Click the "..." button to the right of Physical Path Browse to C:\inetpub\wwwroot Click it Click Make New Folder Call it Emby Click OK Under Binding Fill in with your public host name (see dynamic dns mentioned in pre-reqs) Click OK Configure Logging Click your server Click Logging Click Select Fields Click Add Field Configure as shown Click OK Click OK Click Apply Install and Configure Certify The Web client Download From: https://certifytheweb.com Run the Certify the Web installer Click Next Click Next Click Next Click Install Click Finish Click New Certificate Click on on Contact Prompt Fill in your contact email Click Register Contact Click New Certificate again Select Emby from the sites list Name and domain will populate automatically. Click Deployment Configure as shown Complete certificate verification process Click your site in IIS manager Click Bindings Verify there is an HTTPS binding and that it looks similar to this (with your domain information) Edit Web.Config for Emby Site Click HTTP Response Headers Click Add Configure as show (we are just creating a header to get the web.config to exist, we will paste in a premed one below, so these values dont really matter) Click OK Open an Explorer window and Browse to C:\inetpub\wwwroot\Emby Right click web.config and Edit with Notepad++ Replace existing content with web.config below <?xml version="1.0" encoding="UTF-8"?> <configuration> <system.webServer> <rewrite> <rules> <clear></clear> <rule name="Redirect to https" enabled="true" patternSyntax="Wildcard" stopProcessing="true"> <match url="*" negate="false" /> <conditions logicalGrouping="MatchAny"> <add input="{HTTPS}" pattern="off" /> </conditions> <action type="Redirect" url="https://{HTTP_HOST}{REQUEST_URI}" redirectType="Found" /> </rule> <rule name="Proxy to Emby" stopProcessing="false"> <match url="(.*)" /> <serverVariables> <set name="HTTP_X_ORIGINAL_ACCEPT_ENCODING" value="{HTTP_ACCEPT_ENCODING}" /> <set name="HTTP_ACCEPT_ENCODING" value="" /> <set name="HTTP_X_REAL_IP" value="{REMOTE_ADDR}" /> </serverVariables> <action type="Rewrite" url="http://localhost:8096/{R:1}" logRewrittenUrl="true" /> <conditions> <add input="/{R:1}" pattern=".well-known" negate="true" /> </conditions> </rule> </rules> <outboundRules> <rule name="Add Strict-Transport-Security when HTTPS" enabled="true"> <match serverVariable="RESPONSE_Strict_Transport_Security" pattern=".*" /> <conditions> <add input="{HTTPS}" pattern="on" /> </conditions> <action type="Rewrite" value="max-age=31536000; includeSubDomains; preload" /> </rule> <rule name="Proxy to Emby" preCondition="ResponseIsHtml1" enabled="true"> <match filterByTags="A, Area, Base, Form, Frame, Head, IFrame, Img, Input, Link, Script" pattern="^http(s)?://http://localhost:8096/(.*)" /> <action type="Rewrite" value="http{R:1}://media.example.com/{R:2}" /> </rule> <rule name="Restore-AcceptEncoding" preCondition="NeedsRestoringAcceptEncoding"> <match serverVariable="HTTP_ACCEPT_ENCODING" pattern="^(.*)" /> <action type="Rewrite" value="{HTTP_X_ORIGINAL_ACCEPT_ENCODING}" /> </rule> <preConditions> <preCondition name="ResponseIsHtml1"> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^text/(.+)" /> </preCondition> <preCondition name="NeedsRestoringAcceptEncoding"> <add input="{HTTP_X_ORIGINAL_ACCEPT_ENCODING}" pattern=".+" /> </preCondition> </preConditions> </outboundRules> </rewrite> <caching enabled="false" enableKernelCache="false" /> <httpProtocol> <customHeaders> <add name="X-Frame-Options" value="SAMEORIGIN" /> <add name="X-Xss-Protection" value="1; mode=block" /> <add name="X-Content-Type-Options" value="nosniff" /> <add name="Referrer-Policy" value="same-origin" /> <add name="Feature-Policy" value="sync-xhr 'self'" /> <add name="Cache-Control" value="no-cache" /> </customHeaders> </httpProtocol> </system.webServer> </configuration> Save changes (if prompted to restart Notepad++ in admin mode allow it and then try saving again) IIS will now be properly configured as a reverse proxy for Emby. Under IIS Manager > Rewrite you should now see the following rules: Configure Server Cyphers Download here: https://www.nartac.com/Products/IISCrypto/Download (GUI version) Run the IISCrypto too Click Templates In the template drop down box, select PCI 3.2 This will disable IIS from being able to serve via SSL 2.0, 3.0; TLS 1.0 and TLS 1.1. This will leave just the industry standard TLS 1.2. Click Apply Click OK. Reboot your server. Emby Internal Settings Navigate to your server via the localhost:8096 address Click the gear in the top right corner Click Network from the list of tabs on the right Configure as shown (use your hostname in the external domain box) Conclusion Upon rebooting your computer will start IIS services and Emby server as a service. Traffic coming in on port 80 (if someone just types your url without HTTPS in their browser's address bar) will be automatically redirected to port 443 and the HTTPS:// version of your host name. Your certificate will auto-renew every so often and re-bind to the site in IIS without any interaction on your part. This allows for a server that you can for the most part setup, and forget about and just manage your Emby installation via its web ui. There are a lot of ways to set up Emby server depending on your environment and other factors. For my environment this made the most sense and since large portions of this took quite a bit of digging and research to get working just right, I figured Id make someone else's life a little easier if they were trying to do something similar. These instructions can be adapted for Windows Server 2012 R2, Windows Server 2016, Windows 8 and Windows 10. In the end browsing to your domain should look like this in the browser Additional Information for Updating When Updating your Emby installation. Simply stop the service for Emby, install like you normally would, then just cut the system folder inside the %appdata%\emby-server folder and paste it into the C:\Emby-Server folder. When prompted replace all files, then start the service again once the copy completes. Additional Information about Connecting with Emby Apps When connecting to your Emby installation remotely with Emby apps remember to prefix your domain name with https:// and use 443 for the port number. <Edit> Additional Information about changing Emby Server Title: For those users who wish to change their page title in browser (as discussed here), here is additional Web.Config information that will let you do just that! Using IIS Re-Write rules to change the page title means, you don't have to edit files to reset it every time you upgrade your Emby Server! Add these 3 rules at the bottom of the rules list, replace whole <preConditions> block too.: NOTE: Make sure you replace ALL 4 instances of NAME_OF_YOUR_SERVER with what you want your server to display in the tab bar. <rule name="RewriteTitle" preCondition="ResponseIsHtml1" enabled="true"> <match filterByTags="None" pattern="<title>(.*)</title>" /> <action type="Rewrite" value="<title>NAME_OF_YOUR_SERVER</title>" /> </rule> <rule name="RewriteAppHeaderJs" preCondition="ResponseIsJS" enabled="true"> <match filterByTags="None" pattern="document.title="Emby"" /> <action type="Rewrite" value="document.title="NAME_OF_YOUR_SERVER"" /> </rule> <rule name="RewriteAppHeaderJs2" preCondition="ResponseIsJS" enabled="true"> <match filterByTags="None" pattern="title.Name||"Emby":"Emby"" /> <action type="Rewrite" value="title.Name||"NAME_OF_YOUR_SERVER":"NAME_OF_YOUR_SERVER"" /> </rule> <preConditions> <preCondition name="ResponseIsHtml1"> <add input="{RESPONSE_CONTENT_TYPE}" pattern="^text/(.+)" /> </preCondition> <preCondition name="ResponseIsJS"> <add input="{RESPONSE_CONTENT_TYPE}" pattern="application/javascript|text/javascript" /> </preCondition> <preCondition name="NeedsRestoringAcceptEncoding"> <add input="{HTTP_X_ORIGINAL_ACCEPT_ENCODING}" pattern=".+" /> </preCondition> </preConditions> </Edit>- 121 replies
-
- 15
-

-

-
- how-to
- windows server
- (and 14 more)
-
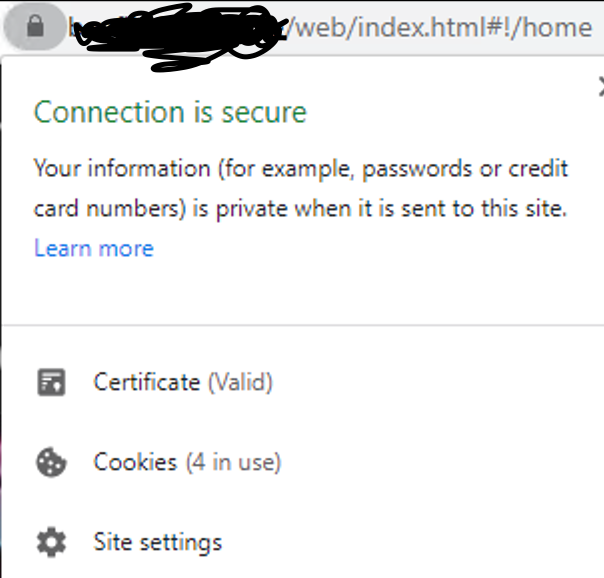
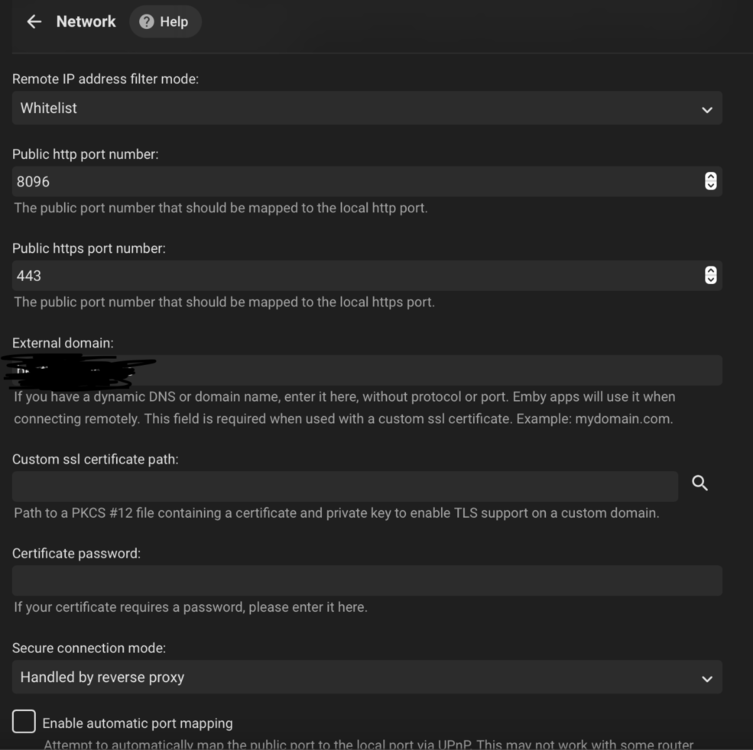
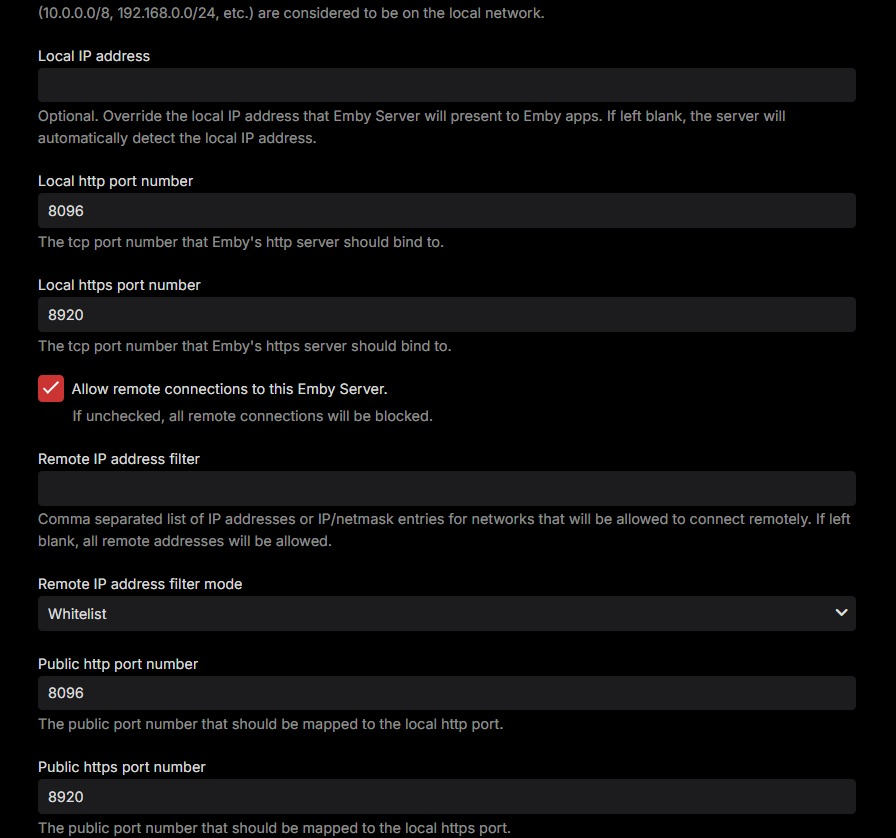
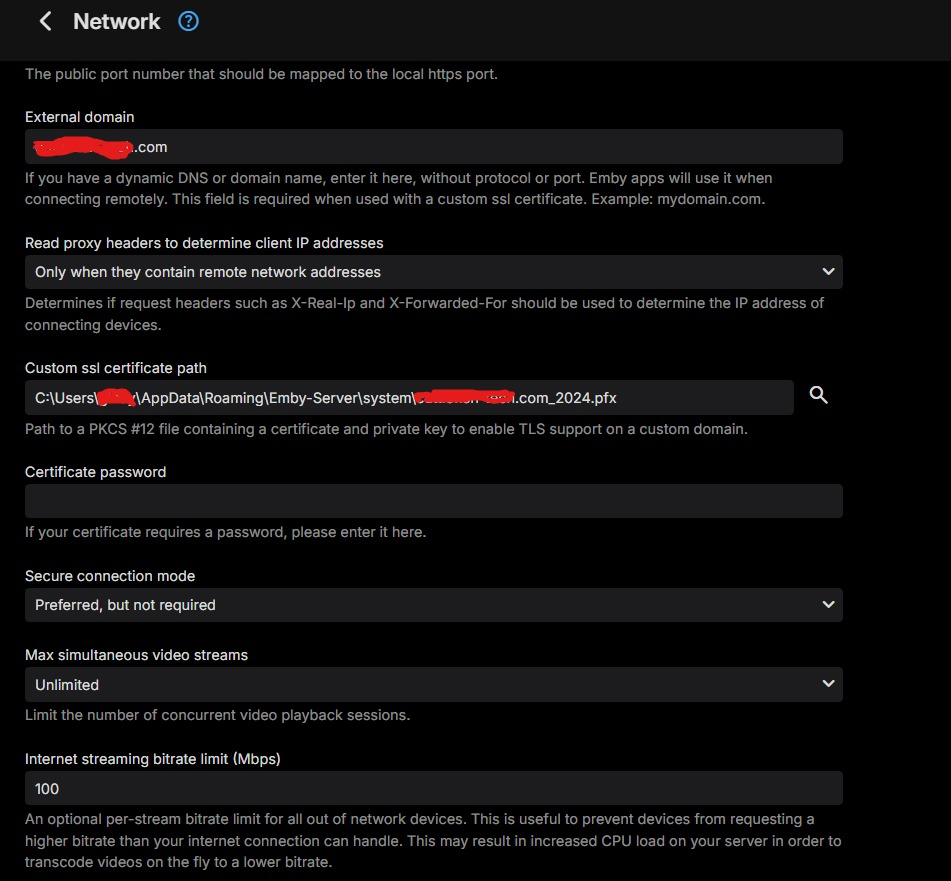
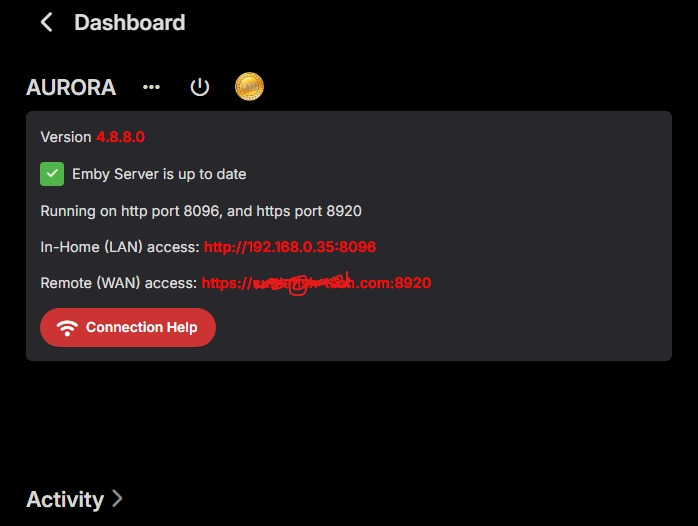
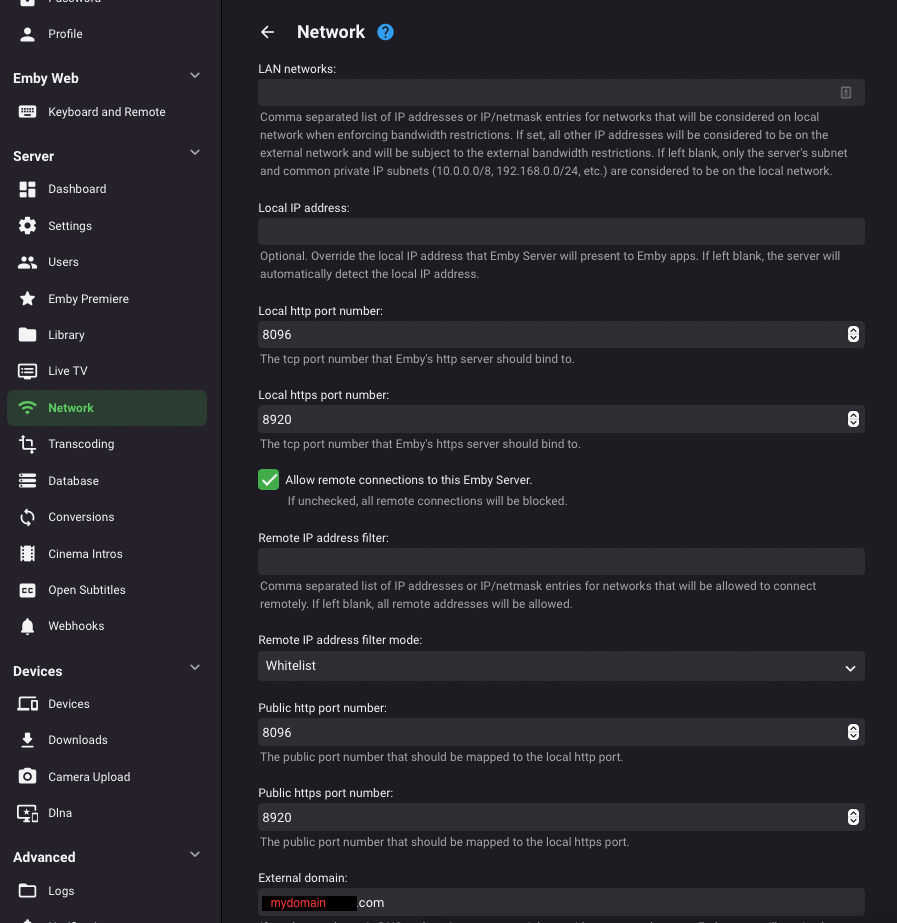
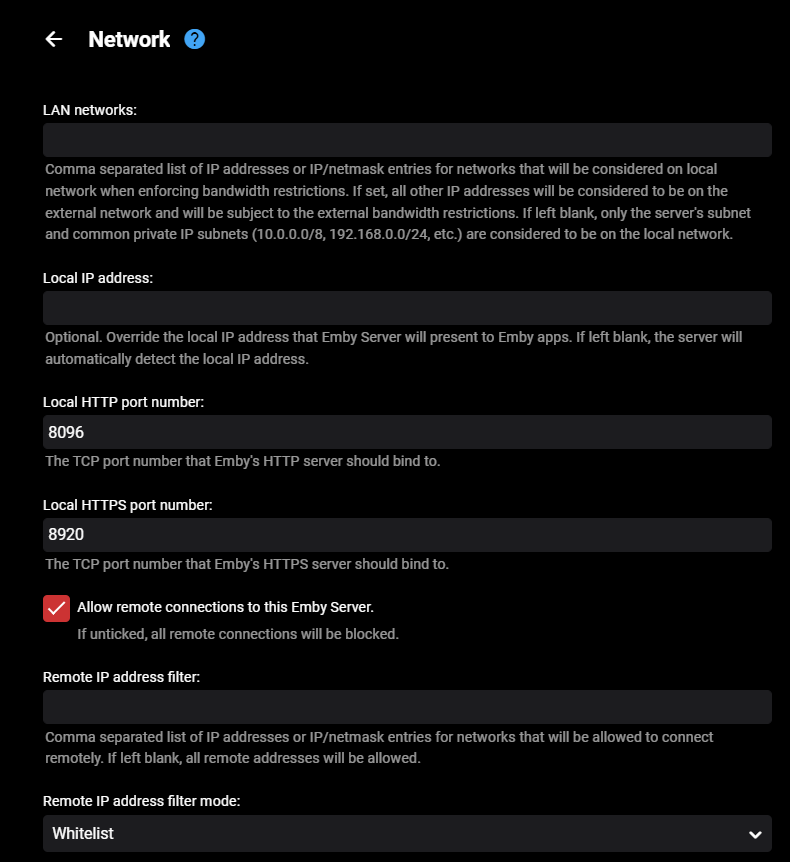
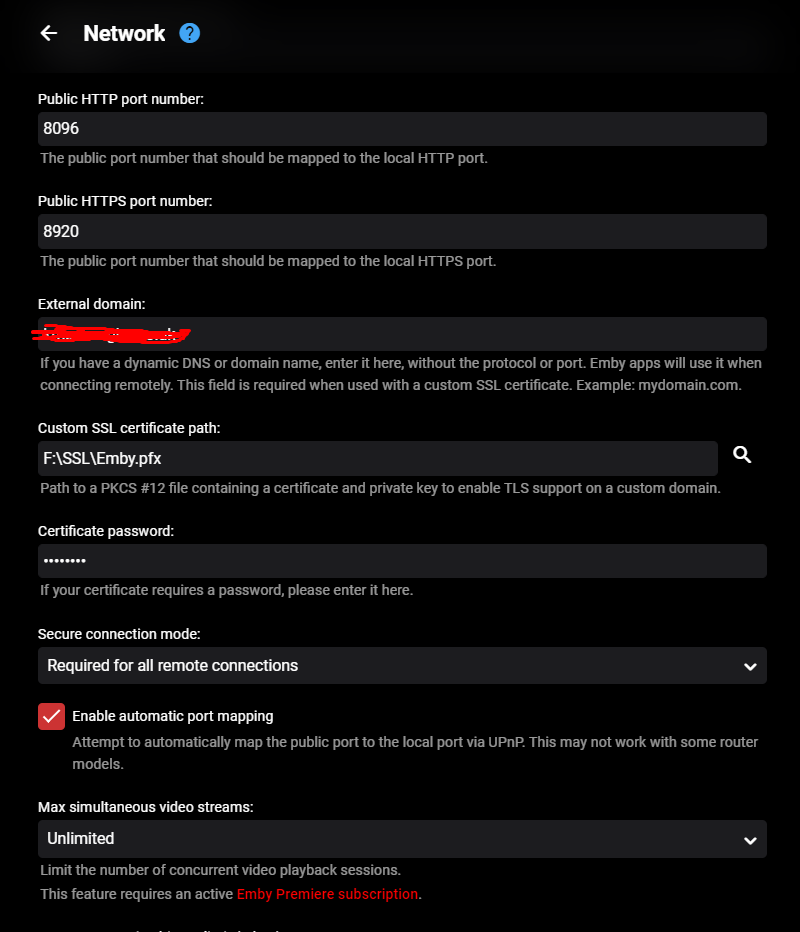
This certificate was specifically created to use Emby through the Microsoft Edge browser over HTTPS on port 8920, eliminating the "connection is not secure" warning. It is important to note that this certificate works properly in Edge but not in Firefox. For the certificate to function correctly, it must be installed both in the Windows Certificate Manager and on the NAS where the Emby server is hosted. Note: The domain names and IPs used here are examples (, ) and must be replaced with those corresponding to your network.example.domain.lansubdomain.local.domain 1. Generate the .crt and .key files Open the Windows terminal: Launch a terminal (Command Prompt or PowerShell) and navigate to the folder where you want to generate the files. Choose the appropriate command based on your needs: For a single domain (single SAN): openssl req -x509 -newkey rsa:2048 -sha256 -days 3650 -nodes -keyout example.domain.lan.key -out example.domain.lan.crt -subj "/CN=example.domain.lan" -addext "subjectAltName=DNS:example.domain.lan" For multiple domains and IPs (multiple SANs): openssl req -x509 -newkey rsa:2048 -sha256 -days 3650 -nodes -keyout example.domain.lan.key -out example.domain.lan.crt -subj "/CN=example.domain.lan" -addext "subjectAltName=DNS:example.domain.lan,DNS:subdomain.local.domain,IP:192.168.1.xx" Verify the results: The files and will be generated in the specified folder. example.domain.lan.crt and example.domain.lan.key 2. Create the .pfx file for Emby Use the following command to merge the and files into a file: .crt + .key = .pfx openssl pkcs12 -export -out example.domain.lan.pfx -inkey example.domain.lan.key -in example.domain.lan.crt -name "example.domain.lan" Set a password for the .pfx file: You’ll be prompted to enter and confirm a password. You can leave it blank or assign one. Note: If you assign a password, remember it, as it will be required in Emby’s settings. The file will be generated in the same folder. example.domain.lan.pfx 3. Upload the .pfx file to the NAS Transfer the file: Copy the file to a folder accessible on your NAS. example.domain.lan.pfx Ensure that Emby can access the path where the file is stored. 4. Install the .crt certificate in Windows Open the .crt file directly: Double-click on the file . example.domain.lan.crt Click the Install Certificate button. Follow the installation wizard: Select Current User as the target location. Choose Place all certificates in the following store. Click Browse and select Trusted Root Certification Authorities. Click OK, then Next, and finally Finish. Confirm the installation: A confirmation message will appear asking if you want to install the certificate. Accept to complete the installation. 5. Configure Emby with the certificate Log in to Emby and navigate to Settings → Network. Locate the section Custom SSL certificate path. Enter the path to the file you uploaded to the NAS..pfx If you set a password for the file, enter it in the corresponding field. If you left it blank, leave the field empty..pfx In Secure connection mode, select: "Preferred, but not required" (this allows connections via both HTTP and HTTPS). Click Save and restart the Emby server to apply the changes. Important Notes The domain names (, ) and IP () are examples. Replace them with the actual domains and IPs of your network.example.domain.lansubdomain.local.domain192.168.1.xx If you need to include more addresses or subdomains, add them to the field when generating the certificate. For example:subjectAltName -addext "subjectAltName=DNS:example.domain.lan,DNS:subdomain.local.domain,DNS:extra.domain.com,IP:192.168.2.xx" Credits This guide was completed with the help and insights provided by @Lessajwhose expertise made this task much easier. Thank you for your support! Final Note If there's anything I missed or ways to improve this guide, I’d greatly appreciate your feedback and insights. Sharing your knowledge or suggesting adjustments would not only help refine this guide but also assist others who might face similar challenges. Feel free to share your thoughts—I'm always open to learning and improving. Thank you in advance!
- 1 reply
-
- 3
-

-
- ssl
- certificate
- (and 4 more)
-

Generate SSL certificate with ASUS router for enabling https on Emby server
teddybear75 posted a topic in General/Windows
So, i needed to enable remote connections for Emby server, and i wanted to secure it with https. I have seen quite a few guides on how to enable https on emby server, but i find this to be an easier way if you own an asus router that supports Lets Encrypt. Im not sure which models that support this, but my AC-86U did. All i did to get a hold of the ssl ceritifactes was to enable this in the WAN-DDNS section in the router, then export files like this: Then i converted the cert and key file to a pfx file with "Win64OpenSSL_Light-1_1_0L" https://slproweb.com/products/Win32OpenSSL.html and imported this in to Emby: I used this command: "openssl pkcs12 -inkey key.pem -in cert.pem -export -out output.pfx" Of course you also have to port forward the needed ports to make this work. Thats it, so if you own an ASUS router with this option you can save a lot of time, and a bonus, the router also automaticly renews the certificates. If this already has been posted i apologize, and feel free to leave comments if there are things i have missed or if this method seems like a bad idea. -
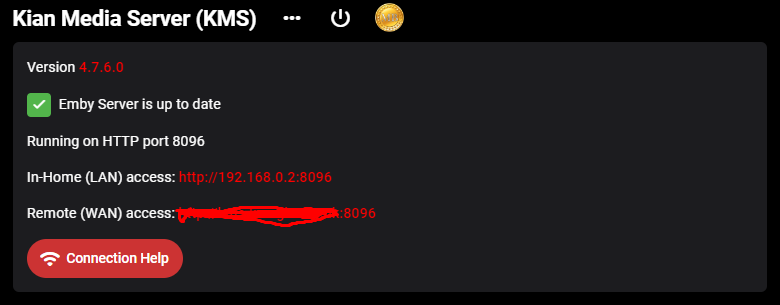
I want to use a sub domain of godaddy to access my emby. It shows it’s not secure when logging in externally. I like to know if the SSL provided by synology for the server also covers emby access? how do I refer to that certificate in emby?
-

Cannot Connect to EMBY Local or Remote using HTTPS on Win 11
gihayes posted a topic in General/Windows
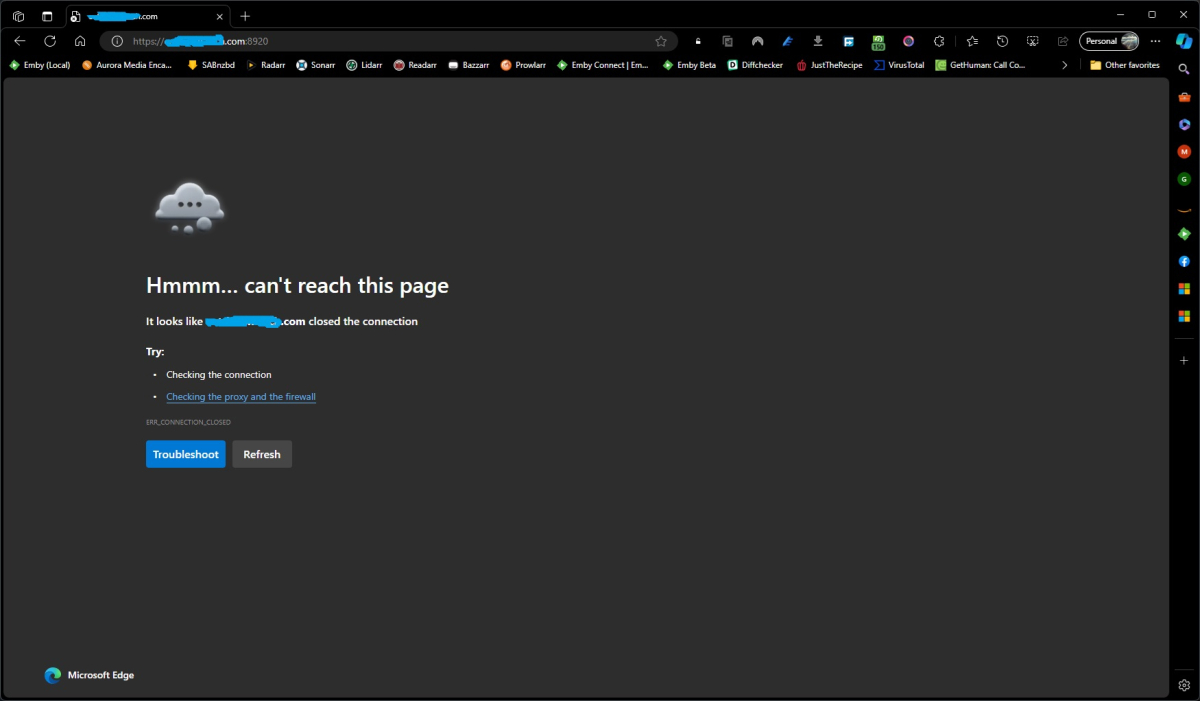
I Have a Domain Name from DYNU and I have been using it for several years with no problems. I bought a Single Domain SSL Certificate from them the other day and have not had any luck getting it to work with EMBY. I downloaded the Certificate files from DYNU and placed the folder with all the files in the EMBY Server system directory. I then pointed EMBY to the .pfx file. See my Emby Network Setup in attached images. The .pfx file that was generated by DYNU does not have a password. My Dashboard shows an https link I have opened port 8920 (and port 443) on my router, but when I configure and attempt to access the site using https, (port 8920 or 443) I get 'Can't Reach This Page' error. I get that regardless if I try to access locally, remotely, with Domain name or IP. I have disabled My Anti-Virus Firewall and Windows Firewall with the same result. I also created a .pfx with a password and tried pointing EMBY to that and it did not work. I have restarted EMBY after each change. A TTL Text Record for my Domain was automatically created when DYNU generated my SSL. My http still works fine, local and remote. I'm at a loss. Is there some step I am missing or something else I need to do? Help. embyserver.txt -
Hello, I wanted I have my emby server running on a server that is accessed by a reverse proxy. This allows me to have multiple domains (other services) under the same IP address. This works great, and I have it running for some time now. Now I would like to enhance the security by adding a required Client Certificate Authentication, so that only authorised personal have access to the server. I configured it on the reverse proxy, and now when I access the server by the Webbrowser (desktop and android) it works, only people that have the certificate installed can communicate with the server. But the app does not work. When I access by the browser it asks me what is the client certificate to use, but in the app I simply can't connect. Is this possible? Or I have some miss configuration? Thank you
- 17 replies
-
- Certificate Authentication
- ssl
-
(and 1 more)
Tagged with:
-
Im using Linux Ubuntu 16.04 64 bit and Asustor AS-604T ADM 3.2.1 This requires you do own a domain and have create a Lets Encrypt certificate! Following ports should be open: 80, 443, 8096 and 8920 1. Login to ADM web interface > Settings > Certificate Manager - Click on Export Certificate. 2. Extract certificate.zip and open the folder certifiate 3. right click in the folder - select open terminal 4. enter the command: * Please change the name of the give-me-a-name.pfx * After execution of this command you will be prompted to create a password, this is recommanded! openssl pkcs12 -export -out give-me-a-name.pfx -inkey ssl.key -in ssl.crt 5. Save the new create give-me-a-name.pfx file on your NAS in a shared folder of own choice 6. go to: http://local.ip.of.nas:8096/ 7. Go to Advanced and do the following Check that Allow remote connection to this Emby Server is marked. * add external domain name * Custon ssl certificate path (Click on the magnifier right to the text field and navigate to where the .pfx file is. * Certificate password - Add the password you entered after execution of step 4. * Secure connection mode - Set to preferred, but not required. 8. Hit save and navigate to Controlpanel > Restart - Now you should be able to access the Emby Media Server from outside.
-
NB: This script only supports debian O/S, and debian based distributions (ubuntu etc). The script requires systemctl and apt which is present in all newer distributions. This script will probably not work as intended on Debian below v7 and Ubuntu below 14. A while back I created a script that will: Check if Apache and/or Nginx is running, and if running stop them. Disable UFW (firewall). Flush iptables. Check if certbot is installed, and if not, install it. Check if certificate is located in the emby directory, and if found, delete it. Ask for your FQDN of your emby server. Create a new certificate that's valid for 90 days. Convert the certificate to PFX and copy it to your emby directory. Ask for your emby group and user and change permissions of the PFX to the specified user (default is emby). Re-enable UFW (firewall). Re-enable Apache and/or Nginx (if it was stopped). Restart the Emby system service. After you have downloaded and placed the script on your server, you must unzip it and give the script execution permission. To do that, run the command: unzip embycert.zip && chmod +x embycert.sh This script should be run every 3 months to keep your certificate up-to-date. This script MUST be run as root with either SU or SUDO. SUDO is not native in Debian, and I would recommend to run this script it as root. NB: After installation, you must define the path to the certificate (under Network tab) which is: /var/lib/emby/emby.pfx and then again manually restart the emby server system service. Remember, if the FQDN is not typed correctly, the installation will fail, so be sure to spell it correctly, and make sure that the A record is valid and working. embycert.sh
- 8 replies
-
- ssl
- letsencrypt
-
(and 4 more)
Tagged with:
-
Do you have a step by step for SSL setup for EMBY?
-
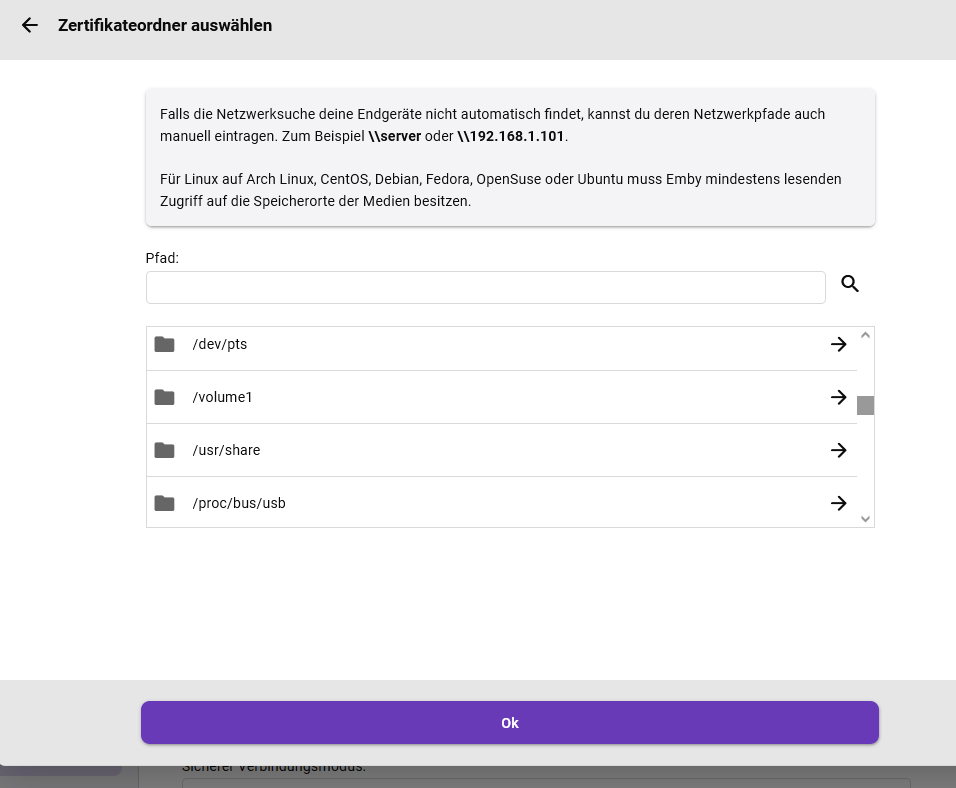
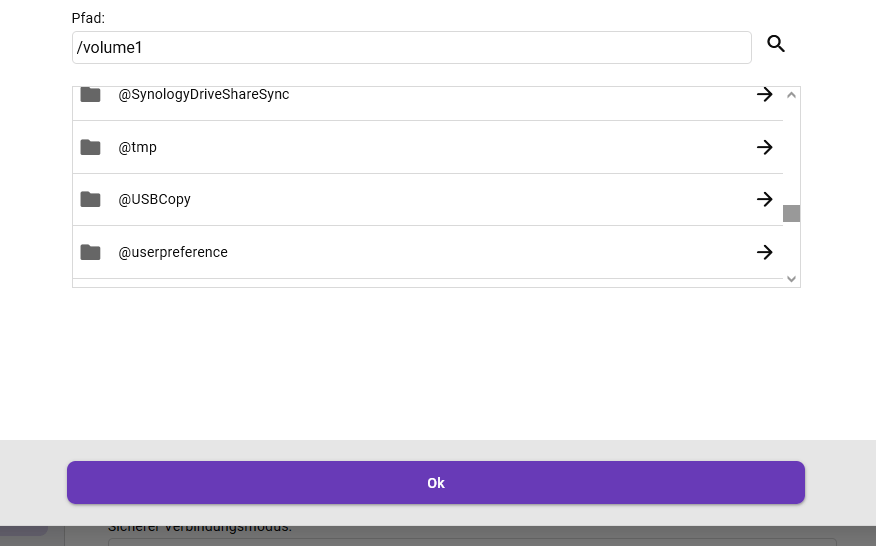
Hi ich hab einen Emby Server auf meinem DS218+ laufen und würde ihn endlich gerne von außerhalb erreichbar machen und auch mit SSL. Mein Syno ist bereits von außen über eine Synology DDNS erreichbar, wie auch die VS, die ja durch den Emby Server ersetzt werden soll. Doch leider kann ich trotz sämtlichen Tutorials den Emby nicht mal über HTTP über meine Domain von außerhalb oder auch innerhalb erreichen.. Getestet hab ich dies mit der aktuellen Androide-App von Emby (Außerhalb wie auch innerhalb des eigenen Netzes). Zudem kann ich aus irgendeinem Grund den Zertifikatspfad auch nicht angeben, bzw. der Emby Server akzeptiert den Pfad nicht, egal wie ich ihn schreibe. Und über die Lupe verschwindet jedes Mal die Ordnerstruktur, sobald ich in einen zweiten Ordner gehe.. (Siehe Bilder) Oder benötige ich damit dies überhaupt funktioniert Emby Primere???? Bin langsam ziemlich ratlos.. embyserver.txt
-
Hi i would like to know if its possible to reuse my certificate LetsEncrypt from my NAS TS-251 to connect through https ? i tried to put the path of the cert certificate but its not working. here is what i have Custom SSL certificate path: /mnt/HDA_ROOT/.config/QcloudSSLCertificate/cert/cert error after restarting EmbyServer 2019-01-05 12:05:44.470 Info AuthenticationRepository: PRAGMA synchronous=1 2019-01-05 12:05:44.526 Error App: No private key included in SSL cert /mnt/HDA_ROOT/.config/QcloudSSLCertificate/cert/cert. 2019-01-05 12:05:44.737 Info ActivityRepository: Default journal_mode for /share/CACHEDEV1_DATA/.qpkg/EmbyServer/programdata/data/activitylog.db is wal and in my web page Secure Connection Failed The connection to xxxxxxxxxxxxxxx.myqnapcloud.com:yyyyyy was interrupted while the page was loading. The page you are trying to view cannot be shown because the authenticity of the received data could not be verified. Please contact the website owners to inform them of this problem. thanks for your help ade05fr
- 26 replies
-
- qnap
- letsencrypt
-
(and 2 more)
Tagged with:
-
I've seen guides for end users to setup secure access to Emby, however this might be more readily adopted if Emby could automatically handle the certificate installation. I found Kestrel/.NET implementation called LettuceEncrypt that might be a good basis to start with.
- 6 replies
-
- 1
-

-
- tls
- encryption
-
(and 3 more)
Tagged with:
-
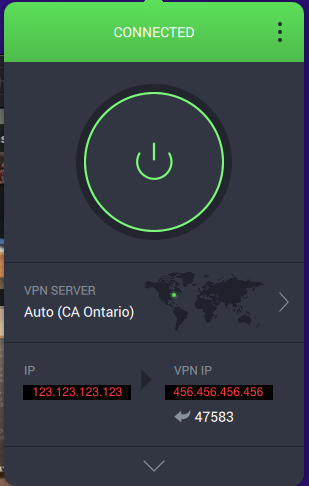
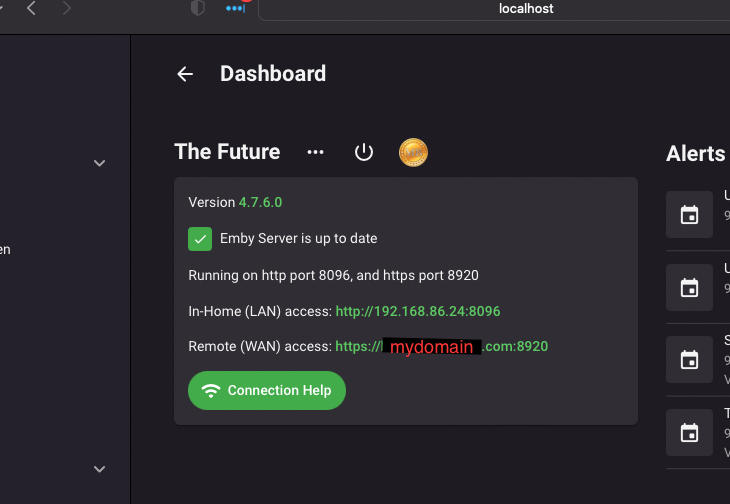
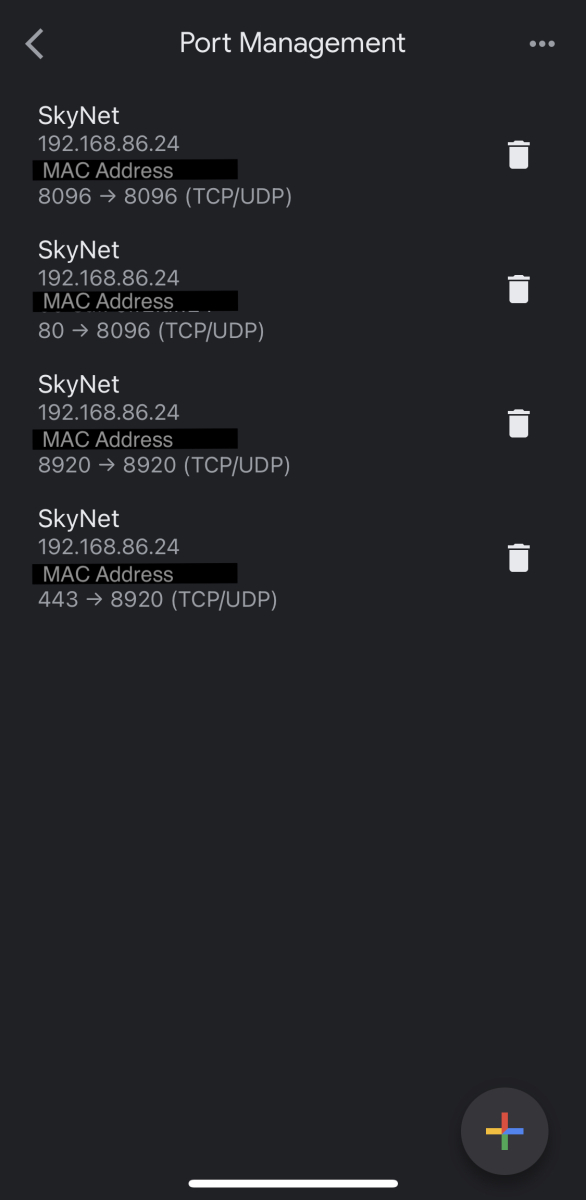
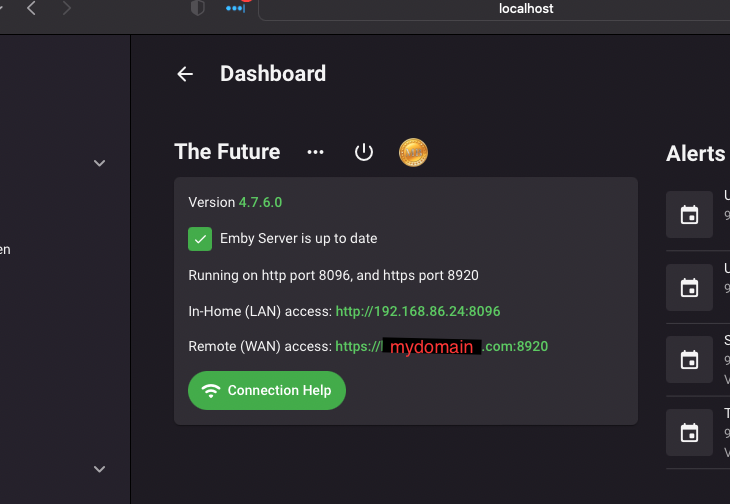
I recently migrated my server from a Windows machine to a Mac mini. I have everything back to how I want it, except for my ability to allow remote connections while I have my VPN (Private Internet Access) running. On my Windows machine, I would use the Split Tunnel to bypass the VPN. Unfortunately, Mac OS seems to have an issue with split tunneling which stops all internet traffic when enabled (a real bummer). So now I am trying to use Port Forwarding as a way to allow connections through my VPN, though I am admittedly not very knowledge about this. I have searched these forums and read numerous threads about this topic, but I have still come away empty-handed. Perhaps someone can look at my specific situation and give me tailored guidance (and perhaps this may serve someone else in the future who faces a similar setup). To begin: I have SSL setup and can allow access to my server via https://mydomain.com. I have forwarded the ports on my router (Google Nest) to allow connections from port 8920 and 443 (as well as 8096 and 80 non-secured ports). When I turn on my VPN with Port-Forwarding enabled, PIA has reserved port 47853, as well as the new IP address of 456.456.456.456. What do I do with this port number and/or VPN IP? On the Emby Network tab I see the local and public https ports are set to 8920. Does one of these change? Or do they stay the same and I need to add a new Port Forwarding rule for 47583? And if I need to add a new rule to my router, do I forward 47583 to 47583 or do I forward 47583 to 8920? Lastly, since I am using SSL and I have my DNS record setup (in Google Domains) to direct mydomain.com to 123.123.123.123 (my ISP assigned IP address), do I also need to update this record so it points to 456.456.456.456 (the VPN IP address when the application is enabled)? (For all intents and purposes, we can treat my ISP IP address as static, technically it is dynamic, but I have a pretty good handle on that part of the process, so I don't want to get caught up in questions away from my main topic regarding the port-forwarding.) If anyone can give me the exact steps of what I need to do, I would very much appreciate it. These forums have been very helpful in the past and I hope to be able to contribute to them in meaningful ways in the future. Thank you.
- 5 replies
-
- port forwarding
- pia vpn
-
(and 2 more)
Tagged with:
-
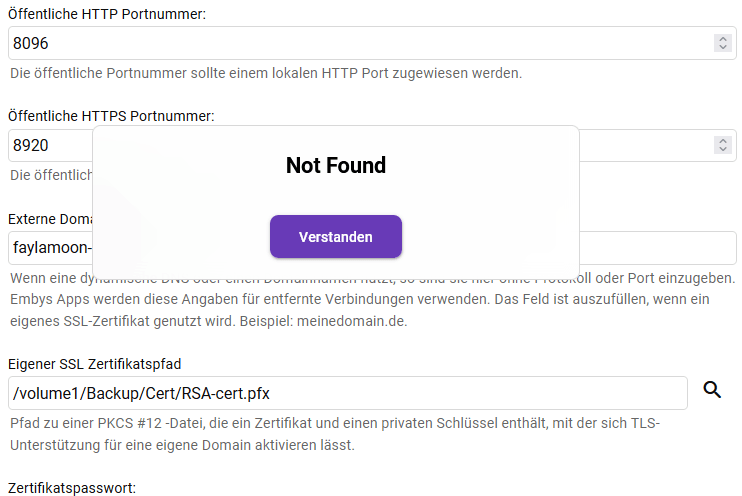
Hello, I'm unable to get SSL to work on my Emby server, I've been able to remote connect on http with no problems but would rather be using TLS. Currently have Emby running on Windows 10, Appropriate ports are open on router. Certificate .PFX created with Certify The Web & exported through IIS. Attached screenshots + log from Emby below, Appreciate any help embyserver.txt
-
I have had Emby for quite a time now and recently bought Emby Premiere so I could use it on more platforms. I have my Emby server running locally on Debian and can connect remotely through my domain (assume my.domain.com). Emby works fine (with SSL) on following the devices I tested: Android app iOS app Windows Store app Xbox One app Most PCs web interface However, I could not get it working with SSL on my LG TV with WebOS 3.5 (LG OLED55B6V if it matters). It did work on a non-secure connection, but when I try to add the server as SSL connection, it simply denies connection like it doesn't even exist. Even when I log onto my Emby Connect account, it simply doesn't show the server, where all other devices do. Now I've read some problems about the SSL certificate (https://emby.media/community/index.php?/topic/57575-lg-emby-app-106-ssl-problem-connecting-to-server/), I'm currently using Comodo PostiveSSL as a certificate, which I have seen at least one other person have problems with as wel. However, I've also seen that some people with Let'sEncrypt have this problem. (https://emby.media/community/index.php?/topic/61481-unable-to-connect-over-https/) There is suggested that LG is simply blocking my certificate, but when I go to my site with the WebOS webbrowser (same certificate), it allows the certificate and shows the site as 'secure'. So somewhere the TV actually does allow the certificate. So I'm not sure where the problem resides. Also, I've shortly tested it on a PS4 from a friend. There was no app, so I used the built-in webbrowser. It also didn't seem to work there, seemed to have the same problem: simply not showing the server. Didn't have much time to test it there, so don't pin me on this. My question is: does anyone have Emby running over SSL with any certificate on LG WebOS 3.5? If so, what certificate do you use?
- 16 replies
-
- SSL
- Certificate
-
(and 5 more)
Tagged with:
-
Hello, I install Emby server on Raspberry pi 4 with Dietpi distro. I have also installed there Nextcloud as my NAS server. There's very easy way to install SSL certificate for Nextcloud. I make a domain myserver.ddns.net on NO-IP website, install certbot and run letsencrypt from dietpi-software. Now I want to add SSL for my Emby Server. I see there's tutorial but I don't know nothing about certificates and don't want to brake something. @@pir8radio @@Swynol Can somebody tell me do I have to make another domain with ddns? There's also information on the tutorial beginning to kill all process on port 80. When I enable https for nextcloud I delete rule for port forwarding on my router for port 80 but when I make command: `netstat -nlp | grep :80` ``` tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 1191/kodi.bin_v8 tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 1032/lighttpd tcp6 0 0 :::8096 :::* LISTEN 26999/EmbyServer tcp6 0 0 :::8080 :::* LISTEN 1191/kodi.bin_v8 tcp6 0 0 :::80 :::* LISTEN 1032/lighttpd ``` Regards Przemek
- 14 replies
-
- dietpi
- raspberry pi
-
(and 1 more)
Tagged with:
-
Hello This is my first post here, but I read here a lot and solved many problems I had, so first thanks this community. But now I have a Problem and no idea how to solve it. I use a lot how-to but I am not able to get an https connection to my Emby Server With this instructions I get no more a "could not connect", but I get a "PR_END_OF_FILE_ERROR" in Firefox and "ERR_CONNECTION_CLOSED" in Chrome. I´m not really familiar with SSL but with an apache or lighttpd I had no problems to set up an https connection, but with the Emby Server I don´t know any further. In the log file there are only the http request, nothing about https. Where should I search for this issue, are there other settings which affect to SSL? If you need more information from me, just ask. BdT Varmandra
-
Looks like my Roku TV 7117X is no longer able to connect to my remote Emby Server via SSL. SSL certificate was generated by Synology Lets Encrypt. I wanted to create this thread to make awareness and so others with same problem can find this. This all seems to be related to the Lets Encrypt certificate issues from September 30. Other clients like IOS app and Chrome browsers can successfully connect with SSL. Looking through other threads other users are reporting with same issues. No sure if there is a way to fix. TCL Roku TV Software Version: 10.0.0 Build 4209-30 Emby App Version 4.0 Build 31
-
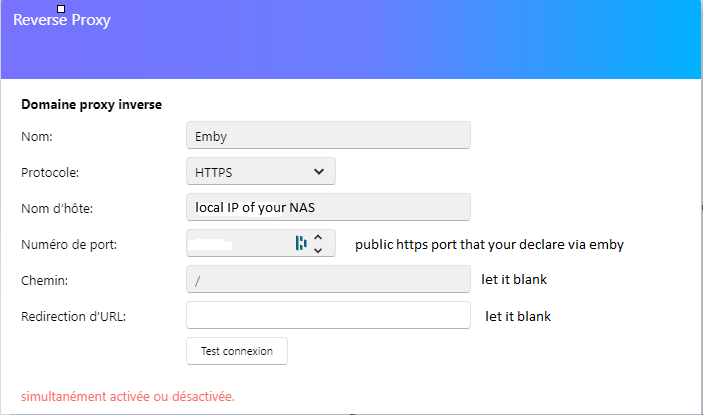
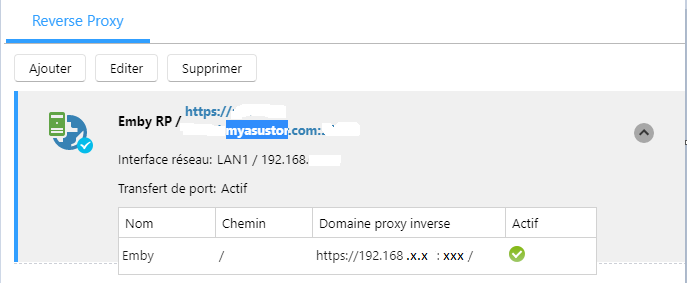
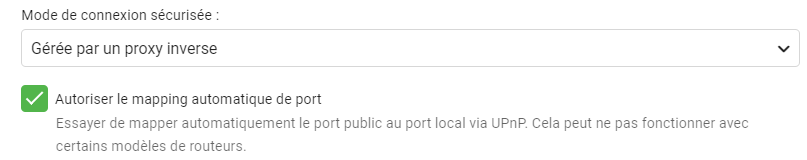
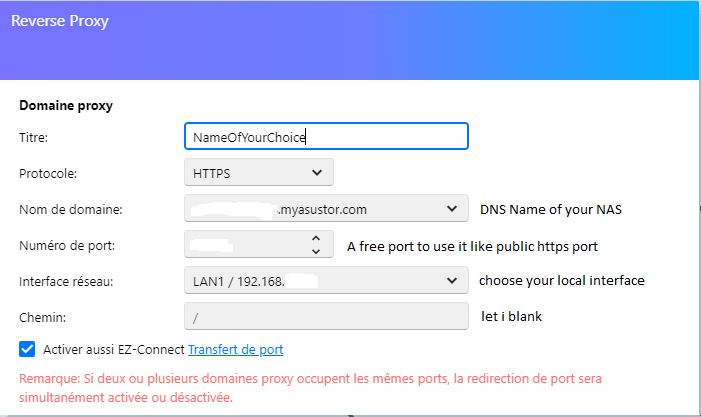
Hello all, If you want to simplify ssl connexion and don't care anymore to renew every 3 months your SSL certificate for emby, you can use reverse proxy like this (i already try to generate it automatically via crontab but i never success to make it work correctly.) Prerequisite : 1 - create the reverse proxy locally on your nas and not remotely 2 - be with adm 4.0, i already try to make it work with 3.5.2 but not working Go to reverse proxy menu and click on add, and fill it like this, fill your own domain name and choose the port that you want. You can use ez connect or declare your redirection directly on your router then click "next" Fill like below and clck on "test connexion" now you have your Emby reverse proxy active and working Under emby network options you can choose this option "managed by a reverse proxy" That's all.
-
I'm trying to set up a load balancer and reverse proxy (Kemp LoadMaster) to handle all incoming connections on port 443 and distribute to my various services in the local network, and to manage SSL certs. I am completely unable to get Emby Server running on macOS to listen on HTTPS. I don't want to "allow remote connections to this Emby Server" or manage an SSL cert on the Emby instance. As you can see below, the Emby Server is not listening on https (port 8920) even though it's reporting that it is. I've tried enabling "allow remote connections" for testing with "handed be reverse proxy" but still no dice. sudo lsof | grep LISTEN | grep -i emby EmbyServe 10196 *redacted* 148u IPv6 0xe964fbfa92b187eb 0t0 TCP *:8096 (LISTEN) embytray 10197 *redacted* 4u IPv4 0xe964fbfa79f4057b 0t0 TCP localhost:8024 (LISTEN) And no, there is nothing else listening on port 8920, and I have tried changing https port to no effect. I'd really like to get this working without using EmbyConnect as I want to manage and monitor internal services through a single interface. Emby Logs: embyserver.txt.zip
-
hi guys my isp has blocked port 80 and I'm unable to authorize my certificates for my ddns. for the sake of the noob users on my network it would be helpful if your apps would automatically accept self signed certificates. i understand this is not possible in web browsers but surely its possible in your apps on smart tv's and consoles etc.... i have recently had to give plex my money which i am not happy about. i dont want to stop supporting emby however if i cant use the secure connections its of no real use to me anymore.
- 3 replies
-
- ssl https letsencrypt
- ssl
-
(and 5 more)
Tagged with:
-
hello, i've been using emby for a little while on my QNAP TS-251B, but recently noticed that my devices (browsers, an nvidia shield) only connect via unsecured http on the default port 8096. when trying to bring up the page (from within my lan) on the default https port of 8920, chrome gives me ERR_CONNECTION_REFUSED. in Emby Configuration > Server > Network, i do see that the port number is indeed set to 8920. however, when i run nmap against the device to scan for open ports, 8920 appears closed. i'm using Emby server version 4.5.4.0