Search the Community
Showing results for tags 'reverse-proxy'.
-
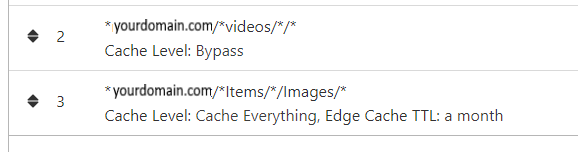
NGINX and emby Config Version 1.0.4 Last Update 1-1-2024 Update by Pir8Radio Why Use NGINX reverse proxy ahead of my application servers like emby? With NGINX or any reverse proxy ahead of an application server you have more control over your setup. You can do things the application servers were not built to handle, have better control over your security and logging, replace lines of code without editing the application server code, better control of caching, etc, etc.... One of the main reasons is so that you don't have to open a new port on your firewall for every application server you host, all you really need to open is 80 & 443 and the internet can reach all of your different servers through one entrance. Will NGINX work on my OS? Most likely, you can find various versions of NGINX for most OS's and they come in different flavors, with options baked in, or just the bare NGINX that you need to compile. See below for download links to get you started. Will NGINX break things on emby? Absolutely if you don't configure it correctly! I HIGHLY suggest when choosing a scheme to setup your domain URL you choose SUB-DOMAIN and NOT sub-directory, more below. Also if you come to the emby forum with things not working, or issues you have and you use a Reverse Proxy, PLEASE make sure that is one of the first things you mention in your forum post. ESPECIALLY if emby works on one platform or client, but not another. So many times people complain "but it works on chrome, so I didn't think it was the reverse proxy". Mention you have a Reverse Proxy please. If the reverse proxy is setup correctly it should be totally transparent to the user and the application server (emby). I'm not going to go into how to purchase and setup a domain name. Lots of how-to's on that out there. Once you have a domain name and its pointed to your IP address, you can go to that domain name and hit your server then continue on.... Sub-Domain vs Sub-Directory: Lets say your domain name is: domain.com there are two main ways you can direct traffic from the internet to your backend application servers like emby. One is sub-directory, something like domain.com/emby or domain.com/other-server This is doable in nginx, but there are some catches and you need to know how your reverse proxy and application server work in detail.. This often breaks different features in emby and other application servers.. To keep with our "Totally Transparent" goal sub-directory doesn't work well, it requires a lot of rewriting and work-arounds to make it work smoothly, if you choose sub-directory you will run into issues you will need to address. The other option is Sub-Domain, this is the cleanest, most transparent, easiest to setup and maintain, it's also what I highly suggest you setup. A sub-domain looks like: emby.domain.com or other-server.domain.com The below config is based on Sub-Domain I will include a sub-directory example as well. NGINX Downloads: Official nginx downloads(LINUX): nginx.org Official nginx downloads(Windows): nginx.org WINDOWS users I suggest this version: nginx-win.ecsds.eu download links are at the bottom of the page. This Windows version has lots of cool features compiled into it already, and is optimized for windows. They keep up with updates, its a FREE (for non-commercial) third party build that I highly recommend. Additional Links: Content Security Policy info (CSP) (For Advanced Users): A CSP WILL break your server if you don't know what you are doing, I suggest reading up, lots of googleing, and understand what a CSP's function is and is not prior to venturing into this area Example NGINX Reverse Proxy Config: 3-29-2020 - ADDED A LINE FOR CLOUDFLARE USERS SO THAT THE X-REAL-IP HEADER IS CORRECTED. THIS ONLY EFFECTS Cloudflare USERS. 4-11-2020 (V1.0.1) - MOVED proxy_buffering off; FROM LOCATION BLOCK TO SERVER BLOCK 12-18-2020 (V1.0.2) - ADDED 301 SERVER SECTION TO FORCE ALL TRAFFIC TO SSL. 9-23-2021 no nginx config change, but cloudflare changed how they cache video files, so emby users that use Cloudflare now need to add a rule like below to make sure video is seekable and playable. 8-18-2022 - added a line for photo sync to cover large uploads of videos and images. (client_max_body_size 1000M;) 1-1-2024 - changed http2 setting per @weblesuggestion in this thread post # 1309363. ** The below "Page Rules" are only needed for Cloudflare CDN users, otherwise ignore. worker_processes auto; error_log logs/error.log; events { worker_connections 8192; } http { include mime.types; default_type application/octet-stream; server_names_hash_bucket_size 64; server_tokens off; ## The below will create a separate log file for your emby server which includes ## userId's and other emby specific info, handy for external log viewers. ## Cloudflare users will want to swap $remote_addr in first line below to $http_CF_Connecting_IP ## to log the real client IP address log_format emby '$remote_addr - $remote_user [$time_local] "$request" ' '$status $body_bytes_sent "$http_referer" ' '"$http_user_agent" "$http_x_forwarded_for" $request_time $server_port "$http_x_emby_authorization"'; log_format default '$remote_addr - $remote_user [$time_local] "$request" ' '$status $body_bytes_sent "$http_referer" ' '"$http_user_agent" "$http_x_forwarded_for" $request_time $server_port'; sendfile off; ## Sendfile not used in a proxy environment. gzip on; ## Compresses the content to the client, speeds up client browsing. gzip_disable "msie6"; gzip_comp_level 6; gzip_min_length 1100; gzip_buffers 16 8k; gzip_proxied any; gzip_types text/plain text/css text/js text/xml text/javascript application/javascript application/x-javascript application/json application/xml application/rss+xml image/svg+xml; proxy_connect_timeout 1h; proxy_send_timeout 1h; proxy_read_timeout 1h; tcp_nodelay on; ## Sends data as fast as it can not buffering large chunks, saves about 200ms per request. ## The below will force all nginx traffic to SSL, make sure all other server blocks only listen on 443 server { listen 80 default_server; server_name _; return 301 https://$host$request_uri; } ## Start of actual server blocks server { listen [::]:443 ssl; ## Listens on port 443 IPv6 ssl enabled listen 443 ssl; ## Listens on port 443 IPv4 ssl enabled http2 on; ## Enables HTTP2 proxy_buffering off; ## Sends data as fast as it can not buffering large chunks. server_name emby.domainname.com; ## enter your service name and domain name here example emby.domainname.com access_log logs/emby.log emby; ## Creates a log file with this name and the log info above. ## SSL SETTINGS ## ssl_session_timeout 30m; ssl_protocols TLSv1.2 TLSv1.1 TLSv1; ssl_certificate ssl/pub.pem; ## Location of your public PEM file. ssl_certificate_key ssl/pvt.pem; ## Location of your private PEM file. ssl_session_cache shared:SSL:10m; location ^~ /swagger { ## Disables access to swagger interface return 404; } location / { proxy_pass http://127.0.0.1:8096; ## Enter the IP and port of the backend emby server here. client_max_body_size 1000M; ## Allows for mobile device large photo uploads. proxy_hide_header X-Powered-By; ## Hides nginx server version from bad guys. proxy_set_header Range $http_range; ## Allows specific chunks of a file to be requested. proxy_set_header If-Range $http_if_range; ## Allows specific chunks of a file to be requested. proxy_set_header X-Real-IP $remote_addr; ## Passes the real client IP to the backend server. #proxy_set_header X-Real-IP $http_CF_Connecting_IP; ## if you use cloudflare un-comment this line and comment out above line. proxy_set_header Host $host; ## Passes the requested domain name to the backend server. proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; ## Adds forwarded IP to the list of IPs that were forwarded to the backend server. ## ADDITIONAL SECURITY SETTINGS ## ## Optional settings to improve security ## ## add these after you have completed your testing and ssl setup ## ## NOTICE: For the Strict-Transport-Security setting below, I would recommend ramping up to this value ## ## See https://hstspreload.org/ read through the "Deployment Recommendations" section first! ## add_header 'Referrer-Policy' 'origin-when-cross-origin'; add_header Strict-Transport-Security "max-age=15552000; preload" always; add_header X-Frame-Options "SAMEORIGIN" always; add_header X-Content-Type-Options "nosniff" always; add_header X-XSS-Protection "1; mode=block" always; ## WEBSOCKET SETTINGS ## Used to pass two way real time info to and from emby and the client. proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection $http_connection; } } }
- 290 replies
-
- 20
-

-

-
- reverse-proxy
- reverse
-
(and 5 more)
Tagged with:
-
Hi guys, I noticed on my main dashboard that my remote access link includes a port at the end when in reality that is not needed. When I went to the network tab and tried to remove the external port, it indicated it was a mandatory field. Issue is when I click the link above for Remote Access (WAN), I get a: ERR_SSL_PROTOCOL_ERROR Ideally my Remote (WAN) access link should be: http://emby.myaddress.myds.me (no port) Does anyone know how to fix this or if its fixable? Thanks!
- 13 replies
-
@pir8radio @pwhodges thanks for trying to help me I have converted Let’s Encrypt to work with emby directly without using Nginx Cer add to emby setting surf to my server and now working without any warning from the browser about the Certificate .. and the video payed as well. ok now when I try with the emby app, the video still give me an error. So it is not related with Nginx ... there is an issue with the app itself @Luke this issue only I have with Galaxy Note 5 The device is Galaxy Note 5 Android 7.0 emby 3.2.56 Server emby 4.7.5.0 (Ubuntu Linux 20.04.4) log file is attached please note that I have replace my domain name and IP to my_domain.com and my_ip on the log file Many Thanks embyserver.txt
- 21 replies
-
- reverse-proxy
- reverse
-
(and 5 more)
Tagged with:
-
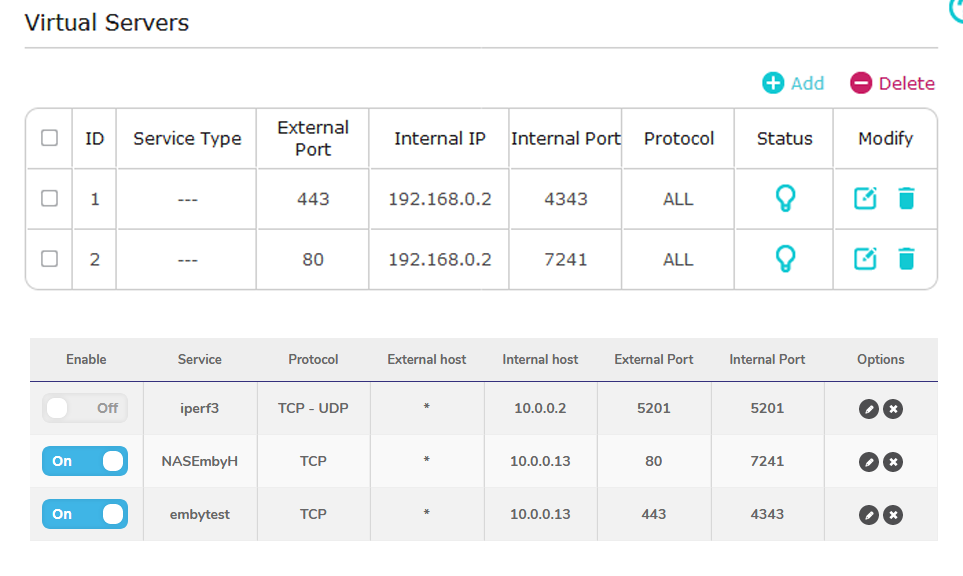
I just got a new router, which means my server has moved from local IP 10.0.x.x to 192.168.x.x. I added exactly the same port-forwarding rules to the new router that I had in the old router, changed the local IP address in the NGINX config, restarted NGINX and...it doesn't connect. The domain gets a CloudFlare 524 error. My IP address followed by ports 80, 443, 4343, 8920 and 7241 fails. My IP address followed by port 8096 succeeds. This doesn't make any sense. I have Emby's ports in the network config set to 4343 for secure and 7241 for non-secure. CanYouSeeMe.org can only see me on port 8096. NGINX isn't jumping in front of any of the attempts at direct-IP access, which from memory it's supposed to.
- 295 replies
-
- reverse-proxy
- reverse
-
(and 5 more)
Tagged with:
-
I'm trying to set up a load balancer and reverse proxy (Kemp LoadMaster) to handle all incoming connections on port 443 and distribute to my various services in the local network, and to manage SSL certs. I am completely unable to get Emby Server running on macOS to listen on HTTPS. I don't want to "allow remote connections to this Emby Server" or manage an SSL cert on the Emby instance. As you can see below, the Emby Server is not listening on https (port 8920) even though it's reporting that it is. I've tried enabling "allow remote connections" for testing with "handed be reverse proxy" but still no dice. sudo lsof | grep LISTEN | grep -i emby EmbyServe 10196 *redacted* 148u IPv6 0xe964fbfa92b187eb 0t0 TCP *:8096 (LISTEN) embytray 10197 *redacted* 4u IPv4 0xe964fbfa79f4057b 0t0 TCP localhost:8024 (LISTEN) And no, there is nothing else listening on port 8920, and I have tried changing https port to no effect. I'd really like to get this working without using EmbyConnect as I want to manage and monitor internal services through a single interface. Emby Logs: embyserver.txt.zip
-
Hi Emby Community, I'm trying to set up a reverse proxy (jada jada jada ipv6 reachable from ipv4 jada jada) and for reasons I can only do it with node.js. I took inspiration from this nginx config guide as there where no guides for node.js but I'm stuck at setting the headers correctly. First I want a working setup in pure node.js and the think about using express for compression middleware and stuff like that. const http = require('http'); const PORT = 80; const hostname = 'emby.mydomain.com'; function onRequest(req, res) { console.log('serve: ' + req.url); const options = { hostname: hostname, port: 80, path: req.url, method: req.method, headers: { ...req.headers, 'X-Real-IP': '$remote_addr', 'X-Forwarded-for': '$proxy_add_x_forwarded_for', 'Host': '$host', 'X-Forwarded-Proto': '$remote_addr', 'X-Forwarded-Protocol': '$scheme', //proxy_redirect off; // websockets //proxy_http_version 1.1; 'Upgrade': '$http_upgrade', 'Connection': "upgrade" } }; const proxy = http.request(options, function (r) { res.writeHead(r.statusCode, r.headers); r.pipe(res, { end: true }); }); req.pipe(proxy, { end: true }); } http.createServer(onRequest).listen(PORT); console.log('Listening on port '+PORT); As I am not very comfortable in nginx and honestly ony a beginner in node.js I'm missing some header information, how to set http to version 1.1 (red something that thats maybe already default?) and how to translate the proxy_redirect directive. Thank you for any responses, maybe someone with some nodejs experience can help me out here.
- 12 replies
-
Stuck Configuring Nginx Reverse Proxy with Cloudflare in front
MachineLearning posted a topic in General/Windows
Inspired by this article on how to host a website using cloudflare and nginx, i intend to do the same for my emby server. Like swynol, i have nginx server and emby server running on the very same machine which i station on my local home network. My OS however is ubuntu instead of windows. Ive tried both swynol's and lukecarrier's github codes, no avail, it wont redirect to the emby server no matter what. My nginx server was indeed running as both ports 80 and 443 are opened as tested by canyouseeme.org. It just wont redirect whenever i go to https://emby.mydomainname.com I dont even know where should i put the code, of the guides online, some say /etc/nginx/conf.d/mydomain.com, some say /etc/nginx/sites-available/mydomain.com with /etc/nginx/sites-enabled linked to earlier. I highly suspect that the code is the culprit. sudo nginx -t show no error, systemctl status nginx operational Shed some light anyone? Appreciate it. Update 16/12/2020 Here's my nginx code where I put under sites-available and then linked to sites-enabled via ln -s server { listen [::]:80; ## Listens on port 80 IPv6 listen 80; ## Listens on port 80 IPv4 listen [::]:443 ssl http2; ## Listens on port 443 IPv6 with http2 and ssl enabled listen 443 ssl http2; ## Listens on port 443 IPv4 with http2 and ssl enabled proxy_buffering off; ## Sends data as fast as it can not buffering large chunks. server_name emby.mydomainname.com; ## enter your service name and domain name here access_log /var/log/nginx/embyaccess.log; ## Creates a log file with this name and the log info above. ## SSL SETTINGS ## ssl_session_timeout 30m; ssl_protocols TLSv1.2 TLSv1.1 TLSv1; ssl_certificate /etc/ssl/mydomainname/cert.pem; ## Location of your public ssl_certificate_key /etc/ssl/mydomainname/key.pem; ## Location of your private PEM file. ssl_client_certificate /etc/ssl/mydomainname/cloudflare.crt; ##Authenticated Origin Pulls ssl_verify_client on; ##Authenticated Origin Pulls ssl_session_cache shared:SSL:10m; location ^~ /swagger { ## Disables access to swagger interface return 404; } location / { proxy_pass http://localhost:8096; ## Enter the IP here proxy_hide_header X-Powered-By; ## Hides nginx server version from bad guys. proxy_set_header Range $http_range; ## Allows specific chunks of a file to be requested. proxy_set_header If-Range $http_if_range; ## Allows specific chunks of a file to be requested. #proxy_set_header X-Real-IP $remote_addr; ## Passes the real client IP to the backend server. proxy_set_header X-Real-IP $http_CF_Connecting_IP; ## if you use cloudflare un-comment this line and comment out above line. proxy_set_header Host $host; ## Passes the requested domain name to the backend server. proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; ## Adds forwarded IP to the list of IPs that were forwarded to the backend server. ## ADDITIONAL SECURITY SETTINGS ## ## Optional settings to improve security ## ## add these after you have completed your testing and ssl setup ## ## NOTICE: For the Strict-Transport-Security setting below, I would recommend ramping up to this value ## ## See https://hstspreload.org/ read through the "Deployment Recommendations" section first! ## add_header 'Referrer-Policy' 'origin-when-cross-origin'; add_header Strict-Transport-Security "max-age=15552000; preload" always; add_header X-Frame-Options "SAMEORIGIN" always; add_header X-Content-Type-Options "nosniff" always; add_header X-XSS-Protection "1; mode=block" always; ## WEBSOCKET SETTINGS ## Used to pass two way real time info to and from emby and the client. proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection $http_connection; } } Big thanks to @pir8radio for the configuration, my configuration is based on his. Setting up authenticated origin pulls is optional, here's where I download the cert. https://support.cloudflare.com/hc/en-us/articles/204899617-Authenticated-Origin-Pulls#section6- 13 replies
-
What I have done so far, I have a domain name purchased from namecheap i'll call it <mydomain> I used namecheap's DDNS on my emby server which creates an A record on the domain. for whatever reason, I had to use www.<mydomain>.com I don't know why but i had to add the www's to get it to work, I had also tried @<mydomain>.com but it would never update I have let this run for a week so everything should be updated and ready to go On my router I forwarded ports 80 and 443 to the emby server with my particular router I can't figure out a way to permit it through the firewall but my test has the firewall turned off so I dont think it is causing the issue. Emby's setting local http 8096 https 8920 public http 80 https 443 allow remote is checked caddy v2 I downloaded the zip, unzipped it on the root directory. Created the extension-less "caddyfile" its contents are, { email <mygmail>@gmail.com } www.<mydomain>.com { reverse_proxy http://192.168.0.18:80 } I know I can use localhost instead of the IP, this should work though because I know it's internal IP and I have it set to not change as I use it to connect using RDP. Running everything I use command prompt and navigate to the Caddy directory with router firewall on and the server's firewall off, I run # caddy run C:\Caddy>caddy run 2020/06/21 14:46:17.402 [34mINFO[0m using adjacent Caddyfile 2020/06/21 14:46:17.413 [34mINFO[0m admin admin endpoint started {"address": "localhost:2019", "enforce_origin": false, "origins": ["localhost:2019"]} 2020/06/21 08:46:17 [INFO][cache:0xc0005ff7c0] Started certificate maintenance routine 2020/06/21 14:46:17.415 [34mINFO[0m http server is listening only on the HTTPS port but has no TLS connection policies; adding one to enable TLS {"server_name": "srv0", "https_port": 443} 2020/06/21 14:46:17.415 [34mINFO[0m http enabling automatic HTTP->HTTPS redirects {"server_name": "srv0"} 2020/06/21 14:46:17.418 [34mINFO[0m tls cleaned up storage units 2020/06/21 14:46:17.418 [34mINFO[0m http enabling automatic TLS certificate management {"domains": ["www.<mydomain>.com"]} 2020/06/21 08:46:17 [INFO][www.<mydomain>.com] Obtain certificate; acquiring lock... 2020/06/21 14:46:17.425 [34mINFO[0m autosaved config {"file": "C:\\Users\\<myuser>\\AppData\\Roaming\\Caddy\\autosave.json"} 2020/06/21 14:46:17.428 [34mINFO[0m serving initial configuration 2020/06/21 08:46:17 [INFO][www.<mydomain>.com] Obtain: Lock acquired; proceeding... 2020/06/21 08:46:17 [INFO][www.<mydomain>.com] Waiting on rate limiter... 2020/06/21 08:46:17 [INFO][www.<mydomain>.com] Done waiting 2020/06/21 08:46:17 [INFO] [www.<mydomain>.com] acme: Obtaining bundled SAN certificate given a CSR 2020/06/21 08:46:18 [INFO] [www.<mydomain>.com] AuthURL: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387022605 2020/06/21 08:46:18 [INFO] [www.<mydomain>.com] acme: Could not find solver for: tls-alpn-01 2020/06/21 08:46:18 [INFO] [www.<mydomain>.com] acme: use http-01 solver 2020/06/21 08:46:18 [INFO] [www.<mydomain>.com] acme: Trying to solve HTTP-01 2020/06/21 08:46:25 [INFO] Deactivating auth: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387022605 2020/06/21 08:46:25 [INFO] Unable to deactivate the authorization: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387022605 2020/06/21 08:46:25 [ERROR] acme: Error -> One or more domains had a problem: [www.<mydomain>.com] acme: error: 400 :: urn:ietf:params:acme:error:connection :: Fetching http://www.<mydomain>.com/.well-known/acme-challenge/P-jvWvwSBjkK_9PQepBe5puAo_TLpsdonnZVunocu-I: Connection reset by peer, url: (challenge=http-01 remaining=[tls-alpn-01]) 2020/06/21 08:46:27 [INFO] [www.<mydomain>.com] acme: Obtaining bundled SAN certificate given a CSR 2020/06/21 08:46:27 [INFO] [www.<mydomain>.com] AuthURL: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387024673 2020/06/21 08:46:27 [INFO] [www.<mydomain>.com] acme: use tls-alpn-01 solver 2020/06/21 08:46:27 [INFO] [www.<mydomain>.com] acme: Trying to solve TLS-ALPN-01 2020/06/21 08:46:28 http: TLS handshake error from 127.0.0.1:61875: EOF 2020/06/21 08:46:28 [INFO] Deactivating auth: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387024673 2020/06/21 08:46:28 [INFO] Unable to deactivate the authorization: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387024673 2020/06/21 08:46:28 [ERROR] acme: Error -> One or more domains had a problem: [www.<mydomain>.com] acme: error: 400 :: urn:ietf:params:acme:error:connection :: Connection refused, url: (challenge=tls-alpn-01 remaining=[]) 2020/06/21 08:46:30 [ERROR] attempt 1: [www.<mydomain>.com] Obtain: [www.<mydomain>.com] acme: Error -> One or more domains had a problem: [www.<mydomain>.com] acme: error: 400 :: urn:ietf:params:acme:error:connection :: Connection refused, url: - retrying in 1m0s (13.0492981s/720h0m0s elapsed)... 2020/06/21 14:46:34.960 [34mINFO[0m shutting down {"signal": "SIGINT"} 2020/06/21 08:46:34 [INFO][cache:0xc0005ff7c0] Stopped certificate maintenance routine 2020/06/21 08:46:34 [INFO][www.<mydomain>.com] Obtain: Releasing lock 2020/06/21 14:46:34.963 [34mINFO[0m shutdown done {"signal": "SIGINT"} with both router and caddy server's firewalls off I run caddy and it does this, C:\Caddy>caddy run 2020/06/21 14:47:55.788 [34mINFO[0m using adjacent Caddyfile 2020/06/21 14:47:55.794 [34mINFO[0m admin admin endpoint started {"address": "localhost:2019", "enforce_origin": false, "origins": ["localhost:2019"]} 2020/06/21 14:47:55.795 [34mINFO[0m http server is listening only on the HTTPS port but has no TLS connection policies; adding one to enable TLS {"server_name": "srv0", "https_port": 443} 2020/06/21 14:47:55.795 [34mINFO[0m http enabling automatic HTTP->HTTPS redirects {"server_name": "srv0"} 2020/06/21 08:47:55 [INFO][cache:0xc0002e3b80] Started certificate maintenance routine 2020/06/21 14:47:55.796 [34mINFO[0m http enabling automatic TLS certificate management {"domains": ["www.<mydomain>.com"]} 2020/06/21 14:47:55.797 [34mINFO[0m tls cleaned up storage units 2020/06/21 14:47:55.798 [34mINFO[0m autosaved config {"file": "C:\\Users\\<myuser>\\AppData\\Roaming\\Caddy\\autosave.json"} 2020/06/21 14:47:55.799 [34mINFO[0m serving initial configuration 2020/06/21 08:47:55 [INFO][www.<mydomain>.com] Obtain certificate; acquiring lock... 2020/06/21 08:47:55 [INFO][www.<mydomain>.com] Obtain: Lock acquired; proceeding... 2020/06/21 08:47:55 [INFO][www.<mydomain>.com] Waiting on rate limiter... 2020/06/21 08:47:55 [INFO][www.<mydomain>.com] Done waiting 2020/06/21 08:47:55 [INFO] [www.<mydomain>.com] acme: Obtaining bundled SAN certificate given a CSR 2020/06/21 08:47:56 [INFO] [www.<mydomain>.com] AuthURL: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387042878 2020/06/21 08:47:56 [INFO] [www.<mydomain>.com] acme: Could not find solver for: tls-alpn-01 2020/06/21 08:47:56 [INFO] [www.<mydomain>.com] acme: use http-01 solver 2020/06/21 08:47:56 [INFO] [www.<mydomain>.com] acme: Trying to solve HTTP-01 2020/06/21 08:48:03 [INFO] Deactivating auth: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387042878 2020/06/21 08:48:03 [INFO] Unable to deactivate the authorization: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387042878 2020/06/21 08:48:03 [ERROR] acme: Error -> One or more domains had a problem: [www.<mydomain>.com] acme: error: 400 :: urn:ietf:params:acme:error:connection :: Fetching http://www.<mydomain>.com/.well-known/acme-challenge/fZqo0DmEmVjo9sElqDlmfJv6r_y50shAJ87QeOgb_rE: Connection reset by peer, url: (challenge=http-01 remaining=[tls-alpn-01]) 2020/06/21 08:48:05 [INFO] [www.<mydomain>.com] acme: Obtaining bundled SAN certificate given a CSR 2020/06/21 08:48:06 [INFO] [www.<mydomain>.com] AuthURL: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387045568 2020/06/21 08:48:06 [INFO] [www.<mydomain>.com] acme: use tls-alpn-01 solver 2020/06/21 08:48:06 [INFO] [www.<mydomain>.com] acme: Trying to solve TLS-ALPN-01 2020/06/21 08:48:06 http: TLS handshake error from 127.0.0.1:62306: EOF 2020/06/21 08:48:11 [INFO] Deactivating auth: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387045568 2020/06/21 08:48:11 [INFO] Unable to deactivate the authorization: https://acme-v02.api.letsencrypt.org/acme/authz-v3/5387045568 2020/06/21 08:48:11 [ERROR] acme: Error -> One or more domains had a problem: [www.<mydomain>.com] acme: error: 400 :: urn:ietf:params:acme:error:connection :: Connection refused, url: (challenge=tls-alpn-01 remaining=[]) 2020/06/21 08:48:13 [ERROR] attempt 1: [www.<mydomain>.com] Obtain: [www.<mydomain>.com] acme: Error -> One or more domains had a problem: [www.<mydomain>.com] acme: error: 400 :: urn:ietf:params:acme:error:connection :: Connection refused, url: - retrying in 1m0s (17.8656781s/720h0m0s elapsed)... 2020/06/21 14:48:24.865 [34mINFO[0m shutting down {"signal": "SIGINT"} 2020/06/21 08:48:24 [INFO][cache:0xc0002e3b80] Stopped certificate maintenance routine 2020/06/21 08:48:24 [INFO][www.<mydomain>.com] Obtain: Releasing lock 2020/06/21 14:48:24.867 [34mINFO[0m shutdown done {"signal": "SIGINT"} The emby server is running windows server 2019 like a lot of server's it doesn't have any additional antivirus or firewall beyond windows defender. This is what I am referring to when I say in the test that the firewall is turned off. Both Private and Public network settings are set to 'Turn off Windows Defender Firewall'. Any help with why this isn't working would be appreciated. If I left out anything that is important please let me know. I am unfamiliar with all of this so if I didn't mention it I almost certainly didn't do it.
- 25 replies
-
After using Emby for a while I'm so happy with it that I decided to publish it to the Internet so I can listen to my music when I'm away, without needing to VPN home. I'm publishing Emby behind a Squid reverse proxy, using SSL termination. Meaning: Internet Client -----HTTPS SSL connection-----> | Squid reverse-proxy -----PLAIN HTTP-----> Emby | INTERNET | LAN Now I have a couple of questions/features requests regarding publishing Emby to the "evil" Internet: Is there any known issue/concern that I should be aware off that is not too relevant while Emby is only visible in the LAN but that can be dangerous if Emby is visible from the Internet? I'm worried about brute force attacks. Is it possible to enable a captcha on the login screen so for example after 3 failed logins the user will need to validate the captcha to try to login again? About the login screen: would it be posible to have a configuration parameter in Emby to "harden" the login form like for example disabling autocomplete on the username field? Is it possible to enable a configuration parameter to hide all users from the login screen, server wide, instead of doing it on user basis only? How does the "in-network sign-in" with the easy pin code works? How does Emby know that the user is logging in from the LAN or from the Internet? What happen if the user is in the Internet but Emby is behind a reverse-proxy in the LAN (all requests comes from the LAN IP of the proxy)? Would Emby check the X-Forwarded-For HTTP header if the reverse-proxy provides it? I know these are a lot of questions and some things may not be even implemented right now, but if they are not, maybe they can be a good idea to implement in the near future since they can help us to protect our server for the "evil" Internet. Cheers