Search the Community
Showing results for tags 'http/2'.
-
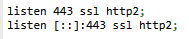
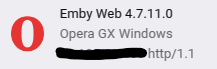
Emby Server Type: Docker Emby Server Version: 4.7.11.0 Reverse Proxy: NGINX Proxy Manager Let's Encrypt Certificate - TLS 1.2, 1.3 Browsers Tested: Firefox, Edge, Chrome, Opera Hello: After looking at some playback, I noticed that my streams are utilizing HTTP/1.1 instead of the far superior HTTP/2 method. I have scoured the forums here as well as Google, and I seem to be alone. My setup is quite simple, with a NGINX Proxy Manager docker that connects clients securely to the Emby server. My domain has HTTP/2 support, with TLS 1.2/1.3 available and established upon client connection. As far as I am aware, the Emby Server Version I am running supports HTTP/2. I see no way to force it in settings, but I know for certain my reverse proxy has it enabled. Could there be any insight as to what I am doing wrong so that HTTP/2 is used? Client ---> TLS 1.3 LE Cert --> NPM ---> Emby:8096
-
I have had a few people ask me to explain how I set up my Apache server to forward to my Emby server. Here is a breakdown of how mine is set up should anyone else wish to try this. This is just my way of doing this (yeah, I know, Nginx exists but I have always been an Apache user). Note that I use RPM based distributions, and my frontend Apache server is running on Fedora Server Edition (so that I can have the http/2 goodness). My instructions will emphasize this type of Linux distribution, so you will need to read up on how your particular flavor of Linux handles Apache installations. First off, here is an overview of my network. Everyone's network is different, but this is what I have set up: edge firewall -> wireless ap/firewall -> apache server -> media server (where the media files are actually stored) On my firewalls, I only have ports 80 and 443 tcp opened up, and they forward to my Apache server. No other ports are exposed to the Internet. My Emby server is not configured with SSL. All SSL is terminated at my Apache server. This way, I can use one SSL certificate to encrypt any web services that I run on my network, without trying to get a certificate for each individual server installation. Anything that comes in on port 80 automatically gets forced over to port 443 (this is done by my Apache server itself). I am also using HTTP/2 which has helped with the various web services that my Apache frontend is exposing to the web. Also, all of my internal servers are running host-based firewalls. There is nothing wrong with security in depth here, and I have personally not heard a valid reason to not run a host-based firewall for your networking services. I use https://letsencrypt.org/ for my SSL certificate. It's free, and their tools are awesome. If you use their services, please donate to them as they are providing a valuable service to practically every community. I also have my own domain name set up and registered, with a dynamic IP from my ISP. There are a plethora of services that will let you register your dynamic IP for a domain name, so search around for the one that suits you best. Personally, I am using Google Domains for mine. My firewall assists in keeping my latest IP registered for my domain. This is extremely handy for mobile devices and family members who wish to use my Emby server remotely. Here are the general steps I would recommend to someone setting this up for themselves: Use an edge firewall. The extra protection is worth it. Use your edge firewall to keep track of your public IP, and use whatever agent that your dynamic DNS provider provides to keep your latest IP registered for your domain. I do not recommend doing this from your Apache server, as your Apache server should be further into your network and protected by your other firewall(s). Set up an SSL certificate for your domain. Again, LetsEncrypt is pretty awesome. Install Apache on a server that can handle a fair amount of network traffic. If you are using LetsEncrypt, set up the agent to keep up with your SSL certificate on this server. dnf groupinstall "Web Server" dnf install mod_http2 Configure your Apache server. On a Fedora, CentOS, RHEL system create a file called /etc/httpd/conf.d/00_yourdomain.conf (the two zeroes are there to make sure that your domain file is loaded first). Here are snippets of my configuration (cleaned up a bit for, you know, security): <VirtualHost *:80> Protocols h2c http/1.1 # Send everything over to https instead, best practice over mod_rewrite ServerName example.com Redirect / https://example.com/ </VirtualHost> <VirtualHost _default_:443> # Enable http/2 Protocols h2 http/1.1 <IfModule http2_module> LogLevel http2:info </IfModule> SSLEngine on SSLProtocol all -SSLv2 -SSLv3 SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:ECDHE-RSA-AES128-SHA:DH-RSA-AES128-GCM-SHA256:AES256+EDH:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4 SSLHonorCipherOrder On SSLCompression off Header always set Strict-Transport-Security "max-age=63072000; includeSubdomains" Header always set X-Frame-Options SAMEORIGIN Header always set X-Content-Type-Options nosniff SSLCertificateFile /etc/letsencrypt/live/example.com/cert.pem SSLCertificateKeyFile /etc/letsencrypt/live/example.com/privkey.pem SSLCertificateChainFile /etc/letsencrypt/live/example.com/fullchain.pem <Files ~ "\.(cgi|shtml|phtml|php3?)$"> SSLOptions +StdEnvVars </Files> <Directory "/var/www/cgi-bin"> SSLOptions +StdEnvVars </Directory> BrowserMatch "MSIE [2-5]" \ nokeepalive ssl-unclean-shutdown \ downgrade-1.0 force-response-1.0 ServerName example.com ServerAlias example.com ErrorLog logs/example-error_log RewriteEngine on RewriteRule ^/emby(.*) http://127.0.0.1:8096/emby$1 [proxy] RewriteRule ^/emby http://127.0.0.1:8096 [proxy] RewriteRule ^/embywebsocket(.*) http://127.0.0.1:8096/embywebsocket$1 [proxy] RewriteRule ^/embywebsocket http://127.0.0.1:8096 [proxy] <location /emby> ProxyPass http://127.0.0.1:8096/ ProxyPassReverse http://127.0.0.1:8096/ </location> <location /embywebsocket> ProxyPass http://127.0.0.1:8096/ ProxyPassReverse http://127.0.0.1:8096/ </location> </VirtualHost> So what this does for me is let Apache handle all incoming port 80 requests, and turns them into encrypted traffic. All connections to and from the server (that can support it) are encapsulated in HTTP/2 packets. All of my SSL encrypted web traffic is handled by one certificate, so I can have multiple URL paths served by the same domain name, with only the https port used, and it just plain looks cleaner. For example, you can have: https://example.com/emby https://example.com/nextcloud https://example.com/hello_kitty_island_adventure Or whatever suits your needs. My Emby server doesn't have to worry about any proxy configurations or SSL, as Apache takes care of all of that. My example is using the localhost IP address to direct all incoming and outgoing Emby requests, but if you are using a separate host that runs Emby, just make sure to use the IP of that system instaed and that you have port 8096 open and available. I hope that others may find this helpful.